What problem does Malware Discoverer address?
URL redirection is a salient feature for phishing and malware sites. Abusers use redirection to control the information flow and to evade detection. Collecting the redirection trace and discovering final URLs that host malicious artifacts is thus not an easy task. One challenge is how to discover entry points, or domains that initiate redirections. Another challenge is how to counteract cloaking techniques including IP-ban, javascript execution and fast flux. Malware Discoverer is designed to handle those challenges.
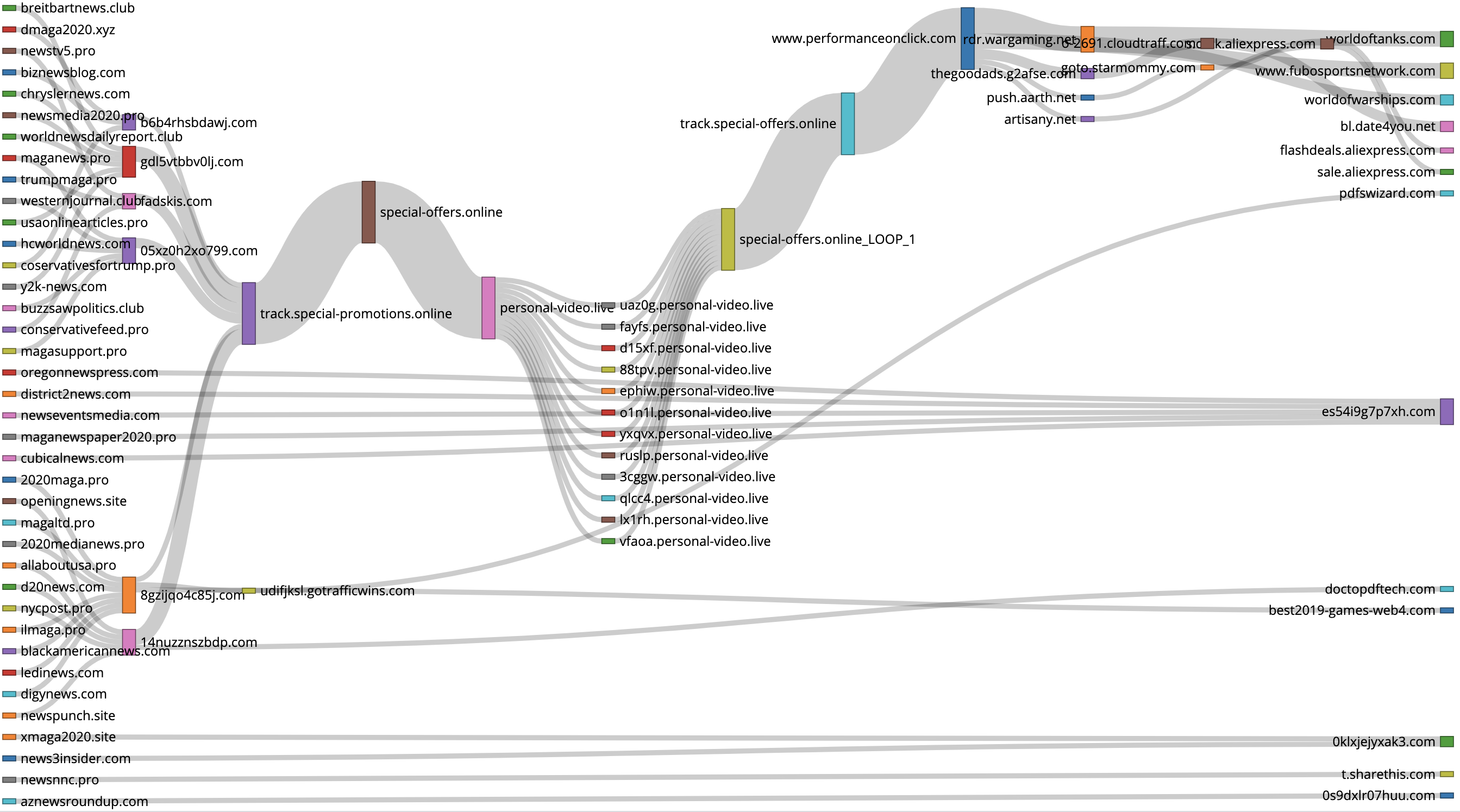 Example of one discovered malware campaigns. The entry-level domains (leftmost) use fake news as bait to lure users to click.
Example of one discovered malware campaigns. The entry-level domains (leftmost) use fake news as bait to lure users to click.
New [2021/12/01]: We are building an interactive version our Malware Discoverer with full API support – try it out and get access to our domain risk API!
New [2021/04/15]: Check out our paper Discovering and Measuring Malicious URL Redirection Campaigns from Fake News Domains, which received the Best Paper Award at the 6th International Workshop on Traffic Measurements for Cybersecurity (WTMC 2021)
New [2021/03/31]: Check out how to add our PUP Domains Blocklist to uBlock Origin, Adguard, etc,. Huge thanks to Ming Di Leom for setting up the feed!
New [2021/03/30]: You can get discovered malicious domains from this blocklist. Currently we only surface domains that lead to PUP (potentially unwanted programs). Other types of malicious domains will be added soon.
New: Malware Discoverer is recommended by RiskIQ and VirusTotal
How does Malware Discoverer work?
Malware Discoverer is powered by an unsupervised discovery system that is able to trace coordinated redirection campaigns. The algorithm includes three components:
- A crawler to collect redirection paths
- A cluster to identify suspicious domains that share common redirection paths
- A search expander to discover more domains co-hosted with suspicious domains
Malware Discoverer is a fully automated system. Currently it is tracking five IP addresses everyday. After the data collection, a python script loads the data, calculates summary statistics, and generates a png of the redirection network (see image above as an example). A daily threat intelligence report is published on this website and sent to subscribers via email.
What do we analyze in the threat intelligence report?
Our reports focus on the coordinated redirection behavior of those malware campaigns. We breakdown domains and IPs into three categories: tier one are entry-level domains/IPs, tier two are intermediate redirection hops, and ther three are final landing domains/IPs. For each tier, the report covers:
- Top 10 domains (registrar, name server, and organization from WHOIS record)
- Top 10 IPs (hostname, city, country, and organization from ipinfo)
- Visualization of redirection network, providing full context about the information flow
- Google Safe Browsing result, Virustotal result
Current data collections and job status
| Date | IP | Andrioid | Chrome | Iphone | Safari |
|---|---|---|---|---|---|
| 2022-07-28 | 64.32.8.68 | ||||
| 2022-07-28 | 37.48.65.149 | ||||
| 2022-07-28 | 207.244.67.215 | ||||
| 2022-07-28 | 103.224.182.207 | ||||
| 2022-07-28 | 185.107.56.59 | ||||
| 2022-07-28 | 93.115.28.104 | ||||
| 2022-07-28 | 74.63.241.23 | ||||
| 2022-07-27 | 64.32.8.68 | ||||
| 2022-07-27 | 37.48.65.149 | ||||
| 2022-07-27 | 207.244.67.215 | ||||
| 2022-07-27 | 103.224.182.207 | ||||
| 2022-07-27 | 185.107.56.59 | ||||
| 2022-07-27 | 93.115.28.104 | ||||
| 2022-07-27 | 74.63.241.23 | ||||
| 2022-07-26 | 64.32.8.68 | ||||
| 2022-07-26 | 37.48.65.149 | ||||
| 2022-07-26 | 207.244.67.215 | ||||
| 2022-07-26 | 103.224.182.207 | ||||
| 2022-07-26 | 185.107.56.59 | ||||
| 2022-07-26 | 93.115.28.104 | ||||
| 2022-07-26 | 74.63.241.23 | ||||
| 2022-07-25 | 64.32.8.68 | ||||
| 2022-07-25 | 37.48.65.149 | ||||
| 2022-07-25 | 207.244.67.215 | ||||
| 2022-07-25 | 103.224.182.207 | ||||
| 2022-07-25 | 185.107.56.59 | ||||
| 2022-07-25 | 93.115.28.104 | ||||
| 2022-07-25 | 74.63.241.23 | ||||
| 2022-07-24 | 64.32.8.68 | ||||
| 2022-07-24 | 37.48.65.149 | ||||
| 2022-07-24 | 207.244.67.215 | ||||
| 2022-07-24 | 103.224.182.207 | ||||
| 2022-07-24 | 185.107.56.59 | ||||
| 2022-07-24 | 93.115.28.104 | ||||
| 2022-07-24 | 74.63.241.23 | ||||
| 2022-07-23 | 64.32.8.68 | ||||
| 2022-07-23 | 37.48.65.149 | ||||
| 2022-07-23 | 207.244.67.215 | ||||
| 2022-07-23 | 103.224.182.207 | ||||
| 2022-07-23 | 185.107.56.59 | ||||
| 2022-07-23 | 93.115.28.104 | ||||
| 2022-07-23 | 74.63.241.23 | ||||
| 2022-07-22 | 64.32.8.68 | ||||
| 2022-07-22 | 37.48.65.149 | ||||
| 2022-07-22 | 207.244.67.215 | ||||
| 2022-07-22 | 103.224.182.207 | ||||
| 2022-07-22 | 185.107.56.59 | ||||
| 2022-07-22 | 93.115.28.104 | ||||
| 2022-07-22 | 74.63.241.23 | ||||
| 2022-07-21 | 64.32.8.68 | ||||
| 2022-07-21 | 37.48.65.149 | ||||
| 2022-07-21 | 207.244.67.215 | ||||
| 2022-07-21 | 103.224.182.207 | ||||
| 2022-07-21 | 185.107.56.59 | ||||
| 2022-07-21 | 93.115.28.104 | ||||
| 2022-07-21 | 74.63.241.23 | ||||
| 2022-07-20 | 64.32.8.68 | ||||
| 2022-07-20 | 37.48.65.149 | ||||
| 2022-07-20 | 207.244.67.215 | ||||
| 2022-07-20 | 103.224.182.207 | ||||
| 2022-07-20 | 185.107.56.59 | ||||
| 2022-07-20 | 93.115.28.104 | ||||
| 2022-07-20 | 74.63.241.23 | ||||
| 2022-07-19 | 64.32.8.68 | ||||
| 2022-07-19 | 37.48.65.149 | ||||
| 2022-07-19 | 207.244.67.215 | ||||
| 2022-07-19 | 103.224.182.207 | ||||
| 2022-07-19 | 185.107.56.59 | ||||
| 2022-07-19 | 93.115.28.104 | ||||
| 2022-07-19 | 74.63.241.23 | ||||
| 2022-07-18 | 64.32.8.68 | ||||
| 2022-07-18 | 37.48.65.149 | ||||
| 2022-07-18 | 207.244.67.215 | ||||
| 2022-07-18 | 103.224.182.207 | ||||
| 2022-07-18 | 185.107.56.59 | ||||
| 2022-07-18 | 93.115.28.104 | ||||
| 2022-07-18 | 74.63.241.23 | ||||
| 2022-07-17 | 64.32.8.68 | ||||
| 2022-07-17 | 37.48.65.149 | ||||
| 2022-07-17 | 207.244.67.215 | ||||
| 2022-07-17 | 103.224.182.207 | ||||
| 2022-07-17 | 185.107.56.59 | ||||
| 2022-07-17 | 93.115.28.104 | ||||
| 2022-07-17 | 74.63.241.23 | ||||
| 2022-07-16 | 64.32.8.68 | ||||
| 2022-07-16 | 37.48.65.149 | ||||
| 2022-07-16 | 207.244.67.215 | ||||
| 2022-07-16 | 103.224.182.207 | ||||
| 2022-07-16 | 185.107.56.59 | ||||
| 2022-07-16 | 93.115.28.104 | ||||
| 2022-07-16 | 74.63.241.23 | ||||
| 2022-07-15 | 64.32.8.68 | ||||
| 2022-07-15 | 37.48.65.149 | ||||
| 2022-07-15 | 207.244.67.215 | ||||
| 2022-07-15 | 103.224.182.207 | ||||
| 2022-07-15 | 185.107.56.59 | ||||
| 2022-07-15 | 93.115.28.104 | ||||
| 2022-07-15 | 74.63.241.23 | ||||
| 2022-07-14 | 64.32.8.68 | ||||
| 2022-07-14 | 37.48.65.149 | ||||
| 2022-07-14 | 207.244.67.215 | ||||
| 2022-07-14 | 103.224.182.207 | ||||
| 2022-07-14 | 185.107.56.59 | ||||
| 2022-07-14 | 93.115.28.104 | ||||
| 2022-07-14 | 74.63.241.23 | ||||
| 2022-07-13 | 64.32.8.68 | ||||
| 2022-07-13 | 37.48.65.149 | ||||
| 2022-07-13 | 207.244.67.215 | ||||
| 2022-07-13 | 103.224.182.207 | ||||
| 2022-07-13 | 185.107.56.59 | ||||
| 2022-07-13 | 93.115.28.104 | ||||
| 2022-07-13 | 74.63.241.23 | ||||
| 2022-07-12 | 64.32.8.68 | ||||
| 2022-07-12 | 37.48.65.149 | ||||
| 2022-07-12 | 207.244.67.215 | ||||
| 2022-07-12 | 103.224.182.207 | ||||
| 2022-07-12 | 185.107.56.59 | ||||
| 2022-07-12 | 93.115.28.104 | ||||
| 2022-07-12 | 74.63.241.23 | ||||
| 2022-07-11 | 64.32.8.68 | ||||
| 2022-07-11 | 37.48.65.149 | ||||
| 2022-07-11 | 207.244.67.215 | ||||
| 2022-07-11 | 103.224.182.207 | ||||
| 2022-07-11 | 185.107.56.59 | ||||
| 2022-07-11 | 93.115.28.104 | ||||
| 2022-07-11 | 74.63.241.23 | ||||
| 2022-07-10 | 64.32.8.68 | ||||
| 2022-07-10 | 37.48.65.149 | ||||
| 2022-07-10 | 207.244.67.215 | ||||
| 2022-07-10 | 103.224.182.207 | ||||
| 2022-07-10 | 185.107.56.59 | ||||
| 2022-07-10 | 93.115.28.104 | ||||
| 2022-07-10 | 74.63.241.23 | ||||
| 2022-07-09 | 64.32.8.68 | ||||
| 2022-07-09 | 37.48.65.149 | ||||
| 2022-07-09 | 207.244.67.215 | ||||
| 2022-07-09 | 103.224.182.207 | ||||
| 2022-07-09 | 185.107.56.59 | ||||
| 2022-07-09 | 93.115.28.104 | ||||
| 2022-07-09 | 74.63.241.23 | ||||
| 2022-07-08 | 64.32.8.68 | ||||
| 2022-07-08 | 37.48.65.149 | ||||
| 2022-07-08 | 207.244.67.215 | ||||
| 2022-07-08 | 103.224.182.207 | ||||
| 2022-07-08 | 185.107.56.59 | ||||
| 2022-07-08 | 93.115.28.104 | ||||
| 2022-07-08 | 74.63.241.23 | ||||
| 2022-07-07 | 64.32.8.68 | ||||
| 2022-07-07 | 37.48.65.149 | ||||
| 2022-07-07 | 207.244.67.215 | ||||
| 2022-07-07 | 103.224.182.207 | ||||
| 2022-07-07 | 185.107.56.59 | ||||
| 2022-07-07 | 93.115.28.104 | ||||
| 2022-07-07 | 74.63.241.23 | ||||
| 2022-07-06 | 64.32.8.68 | ||||
| 2022-07-06 | 37.48.65.149 | ||||
| 2022-07-06 | 207.244.67.215 | ||||
| 2022-07-06 | 103.224.182.207 | ||||
| 2022-07-06 | 185.107.56.59 | ||||
| 2022-07-06 | 93.115.28.104 | ||||
| 2022-07-06 | 74.63.241.23 | ||||
| 2022-07-05 | 64.32.8.68 | ||||
| 2022-07-05 | 37.48.65.149 | ||||
| 2022-07-05 | 207.244.67.215 | ||||
| 2022-07-05 | 103.224.182.207 | ||||
| 2022-07-05 | 185.107.56.59 | ||||
| 2022-07-05 | 93.115.28.104 | ||||
| 2022-07-05 | 74.63.241.23 | ||||
| 2022-07-04 | 64.32.8.68 | ||||
| 2022-07-04 | 37.48.65.149 | ||||
| 2022-07-04 | 207.244.67.215 | ||||
| 2022-07-04 | 103.224.182.207 | ||||
| 2022-07-04 | 185.107.56.59 | ||||
| 2022-07-04 | 93.115.28.104 | ||||
| 2022-07-04 | 74.63.241.23 | ||||
| 2022-07-03 | 64.32.8.68 | ||||
| 2022-07-03 | 37.48.65.149 | ||||
| 2022-07-03 | 207.244.67.215 | ||||
| 2022-07-03 | 103.224.182.207 | ||||
| 2022-07-03 | 185.107.56.59 | ||||
| 2022-07-03 | 93.115.28.104 | ||||
| 2022-07-03 | 74.63.241.23 | ||||
| 2022-07-02 | 64.32.8.68 | ||||
| 2022-07-02 | 37.48.65.149 | ||||
| 2022-07-02 | 207.244.67.215 | ||||
| 2022-07-02 | 103.224.182.207 | ||||
| 2022-07-02 | 185.107.56.59 | ||||
| 2022-07-02 | 93.115.28.104 | ||||
| 2022-07-02 | 74.63.241.23 | ||||
| 2022-07-01 | 64.32.8.68 | ||||
| 2022-07-01 | 37.48.65.149 | ||||
| 2022-07-01 | 207.244.67.215 | ||||
| 2022-07-01 | 103.224.182.207 | ||||
| 2022-07-01 | 185.107.56.59 | ||||
| 2022-07-01 | 93.115.28.104 | ||||
| 2022-07-01 | 74.63.241.23 | ||||
| 2022-06-30 | 64.32.8.68 | ||||
| 2022-06-30 | 37.48.65.149 | ||||
| 2022-06-30 | 207.244.67.215 | ||||
| 2022-06-30 | 103.224.182.207 | ||||
| 2022-06-30 | 185.107.56.59 | ||||
| 2022-06-30 | 93.115.28.104 | ||||
| 2022-06-30 | 74.63.241.23 | ||||
| 2022-06-29 | 64.32.8.68 | ||||
| 2022-06-29 | 37.48.65.149 | ||||
| 2022-06-29 | 207.244.67.215 | ||||
| 2022-06-29 | 103.224.182.207 | ||||
| 2022-06-29 | 185.107.56.59 | ||||
| 2022-06-29 | 93.115.28.104 | ||||
| 2022-06-29 | 74.63.241.23 | ||||
| 2022-06-28 | 64.32.8.68 | ||||
| 2022-06-28 | 37.48.65.149 | ||||
| 2022-06-28 | 207.244.67.215 | ||||
| 2022-06-28 | 103.224.182.207 | ||||
| 2022-06-28 | 185.107.56.59 | ||||
| 2022-06-28 | 93.115.28.104 | ||||
| 2022-06-28 | 74.63.241.23 | ||||
| 2022-06-27 | 64.32.8.68 | ||||
| 2022-06-27 | 37.48.65.149 | ||||
| 2022-06-27 | 207.244.67.215 | ||||
| 2022-06-27 | 103.224.182.207 | ||||
| 2022-06-27 | 185.107.56.59 | ||||
| 2022-06-27 | 93.115.28.104 | ||||
| 2022-06-27 | 74.63.241.23 | ||||
| 2022-06-26 | 64.32.8.68 | ||||
| 2022-06-26 | 37.48.65.149 | ||||
| 2022-06-26 | 207.244.67.215 | ||||
| 2022-06-26 | 103.224.182.207 | ||||
| 2022-06-26 | 185.107.56.59 | ||||
| 2022-06-26 | 93.115.28.104 | ||||
| 2022-06-26 | 74.63.241.23 | ||||
| 2022-06-25 | 64.32.8.68 | ||||
| 2022-06-25 | 37.48.65.149 | ||||
| 2022-06-25 | 207.244.67.215 | ||||
| 2022-06-25 | 103.224.182.207 | ||||
| 2022-06-25 | 185.107.56.59 | ||||
| 2022-06-25 | 93.115.28.104 | ||||
| 2022-06-25 | 74.63.241.23 | ||||
| 2022-06-24 | 64.32.8.68 | ||||
| 2022-06-24 | 37.48.65.149 | ||||
| 2022-06-24 | 207.244.67.215 | ||||
| 2022-06-24 | 103.224.182.207 | ||||
| 2022-06-24 | 185.107.56.59 | ||||
| 2022-06-24 | 93.115.28.104 | ||||
| 2022-06-24 | 74.63.241.23 | ||||
| 2022-06-23 | 64.32.8.68 | ||||
| 2022-06-23 | 37.48.65.149 | ||||
| 2022-06-23 | 207.244.67.215 | ||||
| 2022-06-23 | 103.224.182.207 | ||||
| 2022-06-23 | 185.107.56.59 | ||||
| 2022-06-23 | 93.115.28.104 | ||||
| 2022-06-23 | 74.63.241.23 | ||||
| 2022-06-22 | 64.32.8.68 | ||||
| 2022-06-22 | 37.48.65.149 | ||||
| 2022-06-22 | 207.244.67.215 | ||||
| 2022-06-22 | 103.224.182.207 | ||||
| 2022-06-22 | 185.107.56.59 | ||||
| 2022-06-22 | 93.115.28.104 | ||||
| 2022-06-22 | 74.63.241.23 | ||||
| 2022-06-21 | 64.32.8.68 | ||||
| 2022-06-21 | 37.48.65.149 | ||||
| 2022-06-21 | 207.244.67.215 | ||||
| 2022-06-21 | 103.224.182.207 | ||||
| 2022-06-21 | 185.107.56.59 | ||||
| 2022-06-21 | 93.115.28.104 | ||||
| 2022-06-21 | 74.63.241.23 | ||||
| 2022-06-20 | 64.32.8.68 | ||||
| 2022-06-20 | 37.48.65.149 | ||||
| 2022-06-20 | 207.244.67.215 | ||||
| 2022-06-20 | 103.224.182.207 | ||||
| 2022-06-20 | 185.107.56.59 | ||||
| 2022-06-20 | 93.115.28.104 | ||||
| 2022-06-20 | 74.63.241.23 | ||||
| 2022-06-19 | 64.32.8.68 | ||||
| 2022-06-19 | 37.48.65.149 | ||||
| 2022-06-19 | 207.244.67.215 | ||||
| 2022-06-19 | 103.224.182.207 | ||||
| 2022-06-19 | 185.107.56.59 | ||||
| 2022-06-19 | 93.115.28.104 | ||||
| 2022-06-19 | 74.63.241.23 | ||||
| 2022-06-18 | 64.32.8.68 | ||||
| 2022-06-18 | 37.48.65.149 | ||||
| 2022-06-18 | 207.244.67.215 | ||||
| 2022-06-18 | 103.224.182.207 | ||||
| 2022-06-18 | 185.107.56.59 | ||||
| 2022-06-18 | 93.115.28.104 | ||||
| 2022-06-18 | 74.63.241.23 | ||||
| 2022-06-17 | 64.32.8.68 | ||||
| 2022-06-17 | 37.48.65.149 | ||||
| 2022-06-17 | 207.244.67.215 | ||||
| 2022-06-17 | 103.224.182.207 | ||||
| 2022-06-17 | 185.107.56.59 | ||||
| 2022-06-17 | 93.115.28.104 | ||||
| 2022-06-17 | 74.63.241.23 | ||||
| 2022-06-16 | 64.32.8.68 | ||||
| 2022-06-16 | 37.48.65.149 | ||||
| 2022-06-16 | 207.244.67.215 | ||||
| 2022-06-16 | 103.224.182.207 | ||||
| 2022-06-16 | 185.107.56.59 | ||||
| 2022-06-16 | 93.115.28.104 | ||||
| 2022-06-16 | 74.63.241.23 | ||||
| 2022-06-15 | 64.32.8.68 | ||||
| 2022-06-15 | 37.48.65.149 | ||||
| 2022-06-15 | 207.244.67.215 | ||||
| 2022-06-15 | 103.224.182.207 | ||||
| 2022-06-15 | 185.107.56.59 | ||||
| 2022-06-15 | 93.115.28.104 | ||||
| 2022-06-15 | 74.63.241.23 | ||||
| 2022-06-14 | 64.32.8.68 | ||||
| 2022-06-14 | 37.48.65.149 | ||||
| 2022-06-14 | 207.244.67.215 | ||||
| 2022-06-14 | 103.224.182.207 | ||||
| 2022-06-14 | 185.107.56.59 | ||||
| 2022-06-14 | 93.115.28.104 | ||||
| 2022-06-14 | 74.63.241.23 | ||||
| 2022-06-13 | 64.32.8.68 | ||||
| 2022-06-13 | 37.48.65.149 | ||||
| 2022-06-13 | 207.244.67.215 | ||||
| 2022-06-13 | 103.224.182.207 | ||||
| 2022-06-13 | 185.107.56.59 | ||||
| 2022-06-13 | 93.115.28.104 | ||||
| 2022-06-13 | 74.63.241.23 | ||||
| 2022-06-12 | 64.32.8.68 | ||||
| 2022-06-12 | 37.48.65.149 | ||||
| 2022-06-12 | 207.244.67.215 | ||||
| 2022-06-12 | 103.224.182.207 | ||||
| 2022-06-12 | 185.107.56.59 | ||||
| 2022-06-12 | 93.115.28.104 | ||||
| 2022-06-12 | 74.63.241.23 | ||||
| 2022-06-11 | 64.32.8.68 | ||||
| 2022-06-11 | 37.48.65.149 | ||||
| 2022-06-11 | 207.244.67.215 | ||||
| 2022-06-11 | 103.224.182.207 | ||||
| 2022-06-11 | 185.107.56.59 | ||||
| 2022-06-11 | 93.115.28.104 | ||||
| 2022-06-11 | 74.63.241.23 | ||||
| 2022-06-10 | 64.32.8.68 | ||||
| 2022-06-10 | 37.48.65.149 | ||||
| 2022-06-10 | 207.244.67.215 | ||||
| 2022-06-10 | 103.224.182.207 | ||||
| 2022-06-10 | 185.107.56.59 | ||||
| 2022-06-10 | 93.115.28.104 | ||||
| 2022-06-10 | 74.63.241.23 | ||||
| 2022-06-09 | 64.32.8.68 | ||||
| 2022-06-09 | 37.48.65.149 | ||||
| 2022-06-09 | 207.244.67.215 | ||||
| 2022-06-09 | 103.224.182.207 | ||||
| 2022-06-09 | 185.107.56.59 | ||||
| 2022-06-09 | 93.115.28.104 | ||||
| 2022-06-09 | 74.63.241.23 | ||||
| 2022-06-08 | 64.32.8.68 | ||||
| 2022-06-08 | 37.48.65.149 | ||||
| 2022-06-08 | 207.244.67.215 | ||||
| 2022-06-08 | 103.224.182.207 | ||||
| 2022-06-08 | 185.107.56.59 | ||||
| 2022-06-08 | 93.115.28.104 | ||||
| 2022-06-08 | 74.63.241.23 | ||||
| 2022-06-07 | 64.32.8.68 | ||||
| 2022-06-07 | 37.48.65.149 | ||||
| 2022-06-07 | 207.244.67.215 | ||||
| 2022-06-07 | 103.224.182.207 | ||||
| 2022-06-07 | 185.107.56.59 | ||||
| 2022-06-07 | 93.115.28.104 | ||||
| 2022-06-07 | 74.63.241.23 | ||||
| 2022-06-06 | 64.32.8.68 | ||||
| 2022-06-06 | 37.48.65.149 | ||||
| 2022-06-06 | 207.244.67.215 | ||||
| 2022-06-06 | 103.224.182.207 | ||||
| 2022-06-06 | 185.107.56.59 | ||||
| 2022-06-06 | 93.115.28.104 | ||||
| 2022-06-06 | 74.63.241.23 | ||||
| 2022-06-05 | 64.32.8.68 | ||||
| 2022-06-05 | 37.48.65.149 | ||||
| 2022-06-05 | 207.244.67.215 | ||||
| 2022-06-05 | 103.224.182.207 | ||||
| 2022-06-05 | 185.107.56.59 | ||||
| 2022-06-05 | 93.115.28.104 | ||||
| 2022-06-05 | 74.63.241.23 | ||||
| 2022-06-04 | 64.32.8.68 | ||||
| 2022-06-04 | 37.48.65.149 | ||||
| 2022-06-04 | 207.244.67.215 | ||||
| 2022-06-04 | 103.224.182.207 | ||||
| 2022-06-04 | 185.107.56.59 | ||||
| 2022-06-04 | 93.115.28.104 | ||||
| 2022-06-04 | 74.63.241.23 | ||||
| 2022-06-03 | 64.32.8.68 | ||||
| 2022-06-03 | 37.48.65.149 | ||||
| 2022-06-03 | 207.244.67.215 | ||||
| 2022-06-03 | 103.224.182.207 | ||||
| 2022-06-03 | 185.107.56.59 | ||||
| 2022-06-03 | 93.115.28.104 | ||||
| 2022-06-03 | 74.63.241.23 | ||||
| 2022-06-02 | 64.32.8.68 | ||||
| 2022-06-02 | 37.48.65.149 | ||||
| 2022-06-02 | 207.244.67.215 | ||||
| 2022-06-02 | 103.224.182.207 | ||||
| 2022-06-02 | 185.107.56.59 | ||||
| 2022-06-02 | 93.115.28.104 | ||||
| 2022-06-02 | 74.63.241.23 | ||||
| 2022-06-01 | 64.32.8.68 | ||||
| 2022-06-01 | 37.48.65.149 | ||||
| 2022-06-01 | 207.244.67.215 | ||||
| 2022-06-01 | 103.224.182.207 | ||||
| 2022-06-01 | 185.107.56.59 | ||||
| 2022-06-01 | 93.115.28.104 | ||||
| 2022-06-01 | 74.63.241.23 | ||||
| 2022-05-31 | 64.32.8.68 | ||||
| 2022-05-31 | 37.48.65.149 | ||||
| 2022-05-31 | 207.244.67.215 | ||||
| 2022-05-31 | 103.224.182.207 | ||||
| 2022-05-31 | 185.107.56.59 | ||||
| 2022-05-31 | 93.115.28.104 | ||||
| 2022-05-31 | 74.63.241.23 | ||||
| 2022-05-30 | 64.32.8.68 | ||||
| 2022-05-30 | 37.48.65.149 | ||||
| 2022-05-30 | 207.244.67.215 | ||||
| 2022-05-30 | 103.224.182.207 | ||||
| 2022-05-30 | 185.107.56.59 | ||||
| 2022-05-30 | 93.115.28.104 | ||||
| 2022-05-30 | 74.63.241.23 | ||||
| 2022-05-29 | 64.32.8.68 | ||||
| 2022-05-29 | 37.48.65.149 | ||||
| 2022-05-29 | 207.244.67.215 | ||||
| 2022-05-29 | 103.224.182.207 | ||||
| 2022-05-29 | 185.107.56.59 | ||||
| 2022-05-29 | 93.115.28.104 | ||||
| 2022-05-29 | 74.63.241.23 | ||||
| 2022-05-28 | 64.32.8.68 | ||||
| 2022-05-28 | 37.48.65.149 | ||||
| 2022-05-28 | 207.244.67.215 | ||||
| 2022-05-28 | 103.224.182.207 | ||||
| 2022-05-28 | 185.107.56.59 | ||||
| 2022-05-28 | 93.115.28.104 | ||||
| 2022-05-28 | 74.63.241.23 | ||||
| 2022-05-27 | 64.32.8.68 | ||||
| 2022-05-27 | 37.48.65.149 | ||||
| 2022-05-27 | 207.244.67.215 | ||||
| 2022-05-27 | 103.224.182.207 | ||||
| 2022-05-27 | 185.107.56.59 | ||||
| 2022-05-27 | 93.115.28.104 | ||||
| 2022-05-27 | 74.63.241.23 | ||||
| 2022-05-26 | 64.32.8.68 | ||||
| 2022-05-26 | 37.48.65.149 | ||||
| 2022-05-26 | 207.244.67.215 | ||||
| 2022-05-26 | 103.224.182.207 | ||||
| 2022-05-26 | 185.107.56.59 | ||||
| 2022-05-26 | 93.115.28.104 | ||||
| 2022-05-26 | 74.63.241.23 | ||||
| 2022-05-25 | 64.32.8.68 | ||||
| 2022-05-25 | 37.48.65.149 | ||||
| 2022-05-25 | 207.244.67.215 | ||||
| 2022-05-25 | 103.224.182.207 | ||||
| 2022-05-25 | 185.107.56.59 | ||||
| 2022-05-25 | 93.115.28.104 | ||||
| 2022-05-25 | 74.63.241.23 | ||||
| 2022-05-24 | 64.32.8.68 | ||||
| 2022-05-24 | 37.48.65.149 | ||||
| 2022-05-24 | 207.244.67.215 | ||||
| 2022-05-24 | 103.224.182.207 | ||||
| 2022-05-24 | 185.107.56.59 | ||||
| 2022-05-24 | 93.115.28.104 | ||||
| 2022-05-24 | 74.63.241.23 | ||||
| 2022-05-23 | 64.32.8.68 | ||||
| 2022-05-23 | 37.48.65.149 | ||||
| 2022-05-23 | 207.244.67.215 | ||||
| 2022-05-23 | 103.224.182.207 | ||||
| 2022-05-23 | 185.107.56.59 | ||||
| 2022-05-23 | 93.115.28.104 | ||||
| 2022-05-23 | 74.63.241.23 | ||||
| 2022-05-22 | 64.32.8.68 | ||||
| 2022-05-22 | 37.48.65.149 | ||||
| 2022-05-22 | 207.244.67.215 | ||||
| 2022-05-22 | 103.224.182.207 | ||||
| 2022-05-22 | 185.107.56.59 | ||||
| 2022-05-22 | 93.115.28.104 | ||||
| 2022-05-22 | 74.63.241.23 | ||||
| 2022-05-21 | 64.32.8.68 | ||||
| 2022-05-21 | 37.48.65.149 | ||||
| 2022-05-21 | 207.244.67.215 | ||||
| 2022-05-21 | 103.224.182.207 | ||||
| 2022-05-21 | 185.107.56.59 | ||||
| 2022-05-21 | 93.115.28.104 | ||||
| 2022-05-21 | 74.63.241.23 | ||||
| 2022-05-20 | 64.32.8.68 | ||||
| 2022-05-20 | 37.48.65.149 | ||||
| 2022-05-20 | 207.244.67.215 | ||||
| 2022-05-20 | 103.224.182.207 | ||||
| 2022-05-20 | 185.107.56.59 | ||||
| 2022-05-20 | 93.115.28.104 | ||||
| 2022-05-20 | 74.63.241.23 | ||||
| 2022-05-19 | 64.32.8.68 | ||||
| 2022-05-19 | 37.48.65.149 | ||||
| 2022-05-19 | 207.244.67.215 | ||||
| 2022-05-19 | 103.224.182.207 | ||||
| 2022-05-19 | 185.107.56.59 | ||||
| 2022-05-19 | 93.115.28.104 | ||||
| 2022-05-19 | 74.63.241.23 | ||||
| 2022-05-18 | 64.32.8.68 | ||||
| 2022-05-18 | 37.48.65.149 | ||||
| 2022-05-18 | 207.244.67.215 | ||||
| 2022-05-18 | 103.224.182.207 | ||||
| 2022-05-18 | 185.107.56.59 | ||||
| 2022-05-18 | 93.115.28.104 | ||||
| 2022-05-18 | 74.63.241.23 | ||||
| 2022-05-17 | 64.32.8.68 | ||||
| 2022-05-17 | 37.48.65.149 | ||||
| 2022-05-17 | 207.244.67.215 | ||||
| 2022-05-17 | 103.224.182.207 | ||||
| 2022-05-17 | 185.107.56.59 | ||||
| 2022-05-17 | 93.115.28.104 | ||||
| 2022-05-17 | 74.63.241.23 | ||||
| 2022-05-16 | 64.32.8.68 | ||||
| 2022-05-16 | 37.48.65.149 | ||||
| 2022-05-16 | 207.244.67.215 | ||||
| 2022-05-16 | 103.224.182.207 | ||||
| 2022-05-16 | 185.107.56.59 | ||||
| 2022-05-16 | 93.115.28.104 | ||||
| 2022-05-16 | 74.63.241.23 | ||||
| 2022-05-15 | 64.32.8.68 | ||||
| 2022-05-15 | 37.48.65.149 | ||||
| 2022-05-15 | 207.244.67.215 | ||||
| 2022-05-15 | 103.224.182.207 | ||||
| 2022-05-15 | 185.107.56.59 | ||||
| 2022-05-15 | 93.115.28.104 | ||||
| 2022-05-15 | 74.63.241.23 | ||||
| 2022-05-14 | 64.32.8.68 | ||||
| 2022-05-14 | 37.48.65.149 | ||||
| 2022-05-14 | 207.244.67.215 | ||||
| 2022-05-14 | 103.224.182.207 | ||||
| 2022-05-14 | 185.107.56.59 | ||||
| 2022-05-14 | 93.115.28.104 | ||||
| 2022-05-14 | 74.63.241.23 | ||||
| 2022-05-13 | 64.32.8.68 | ||||
| 2022-05-13 | 37.48.65.149 | ||||
| 2022-05-13 | 207.244.67.215 | ||||
| 2022-05-13 | 103.224.182.207 | ||||
| 2022-05-13 | 185.107.56.59 | ||||
| 2022-05-13 | 93.115.28.104 | ||||
| 2022-05-13 | 74.63.241.23 | ||||
| 2022-05-12 | 64.32.8.68 | ||||
| 2022-05-12 | 37.48.65.149 | ||||
| 2022-05-12 | 207.244.67.215 | ||||
| 2022-05-12 | 103.224.182.207 | ||||
| 2022-05-12 | 185.107.56.59 | ||||
| 2022-05-12 | 93.115.28.104 | ||||
| 2022-05-12 | 74.63.241.23 | ||||
| 2022-05-11 | 64.32.8.68 | ||||
| 2022-05-11 | 37.48.65.149 | ||||
| 2022-05-11 | 207.244.67.215 | ||||
| 2022-05-11 | 103.224.182.207 | ||||
| 2022-05-11 | 185.107.56.59 | ||||
| 2022-05-11 | 93.115.28.104 | ||||
| 2022-05-11 | 74.63.241.23 | ||||
| 2022-05-10 | 64.32.8.68 | ||||
| 2022-05-10 | 37.48.65.149 | ||||
| 2022-05-10 | 207.244.67.215 | ||||
| 2022-05-10 | 103.224.182.207 | ||||
| 2022-05-10 | 185.107.56.59 | ||||
| 2022-05-10 | 93.115.28.104 | ||||
| 2022-05-10 | 74.63.241.23 | ||||
| 2022-05-09 | 64.32.8.68 | ||||
| 2022-05-09 | 37.48.65.149 | ||||
| 2022-05-09 | 207.244.67.215 | ||||
| 2022-05-09 | 103.224.182.207 | ||||
| 2022-05-09 | 185.107.56.59 | ||||
| 2022-05-09 | 93.115.28.104 | ||||
| 2022-05-09 | 74.63.241.23 | ||||
| 2022-05-08 | 64.32.8.68 | ||||
| 2022-05-08 | 37.48.65.149 | ||||
| 2022-05-08 | 207.244.67.215 | ||||
| 2022-05-08 | 103.224.182.207 | ||||
| 2022-05-08 | 185.107.56.59 | ||||
| 2022-05-08 | 93.115.28.104 | ||||
| 2022-05-08 | 74.63.241.23 | ||||
| 2022-05-07 | 64.32.8.68 | ||||
| 2022-05-07 | 37.48.65.149 | ||||
| 2022-05-07 | 207.244.67.215 | ||||
| 2022-05-07 | 103.224.182.207 | ||||
| 2022-05-07 | 185.107.56.59 | ||||
| 2022-05-07 | 93.115.28.104 | ||||
| 2022-05-07 | 74.63.241.23 | ||||
| 2022-05-06 | 64.32.8.68 | ||||
| 2022-05-06 | 37.48.65.149 | ||||
| 2022-05-06 | 207.244.67.215 | ||||
| 2022-05-06 | 103.224.182.207 | ||||
| 2022-05-06 | 185.107.56.59 | ||||
| 2022-05-06 | 93.115.28.104 | ||||
| 2022-05-06 | 74.63.241.23 | ||||
| 2022-05-05 | 64.32.8.68 | ||||
| 2022-05-05 | 37.48.65.149 | ||||
| 2022-05-05 | 207.244.67.215 | ||||
| 2022-05-05 | 103.224.182.207 | ||||
| 2022-05-05 | 185.107.56.59 | ||||
| 2022-05-05 | 93.115.28.104 | ||||
| 2022-05-05 | 74.63.241.23 | ||||
| 2022-05-04 | 64.32.8.68 | ||||
| 2022-05-04 | 37.48.65.149 | ||||
| 2022-05-04 | 207.244.67.215 | ||||
| 2022-05-04 | 103.224.182.207 | ||||
| 2022-05-04 | 185.107.56.59 | ||||
| 2022-05-04 | 93.115.28.104 | ||||
| 2022-05-04 | 74.63.241.23 | ||||
| 2022-05-03 | 64.32.8.68 | ||||
| 2022-05-03 | 37.48.65.149 | ||||
| 2022-05-03 | 207.244.67.215 | ||||
| 2022-05-03 | 103.224.182.207 | ||||
| 2022-05-03 | 185.107.56.59 | ||||
| 2022-05-03 | 93.115.28.104 | ||||
| 2022-05-03 | 74.63.241.23 | ||||
| 2022-05-02 | 64.32.8.68 | ||||
| 2022-05-02 | 37.48.65.149 | ||||
| 2022-05-02 | 207.244.67.215 | ||||
| 2022-05-02 | 103.224.182.207 | ||||
| 2022-05-02 | 185.107.56.59 | ||||
| 2022-05-02 | 93.115.28.104 | ||||
| 2022-05-02 | 74.63.241.23 | ||||
| 2022-05-01 | 64.32.8.68 | ||||
| 2022-05-01 | 37.48.65.149 | ||||
| 2022-05-01 | 207.244.67.215 | ||||
| 2022-05-01 | 103.224.182.207 | ||||
| 2022-05-01 | 185.107.56.59 | ||||
| 2022-05-01 | 93.115.28.104 | ||||
| 2022-05-01 | 74.63.241.23 | ||||
| 2022-04-30 | 64.32.8.68 | ||||
| 2022-04-30 | 37.48.65.149 | ||||
| 2022-04-30 | 207.244.67.215 | ||||
| 2022-04-30 | 103.224.182.207 | ||||
| 2022-04-30 | 185.107.56.59 | ||||
| 2022-04-30 | 93.115.28.104 | ||||
| 2022-04-30 | 74.63.241.23 | ||||
| 2022-04-29 | 64.32.8.68 | ||||
| 2022-04-29 | 37.48.65.149 | ||||
| 2022-04-29 | 207.244.67.215 | ||||
| 2022-04-29 | 103.224.182.207 | ||||
| 2022-04-29 | 185.107.56.59 | ||||
| 2022-04-29 | 93.115.28.104 | ||||
| 2022-04-29 | 74.63.241.23 | ||||
| 2022-04-28 | 64.32.8.68 | ||||
| 2022-04-28 | 37.48.65.149 | ||||
| 2022-04-28 | 207.244.67.215 | ||||
| 2022-04-28 | 103.224.182.207 | ||||
| 2022-04-28 | 185.107.56.59 | ||||
| 2022-04-28 | 93.115.28.104 | ||||
| 2022-04-28 | 74.63.241.23 | ||||
| 2022-04-27 | 64.32.8.68 | ||||
| 2022-04-27 | 37.48.65.149 | ||||
| 2022-04-27 | 207.244.67.215 | ||||
| 2022-04-27 | 103.224.182.207 | ||||
| 2022-04-27 | 185.107.56.59 | ||||
| 2022-04-27 | 93.115.28.104 | ||||
| 2022-04-27 | 74.63.241.23 | ||||
| 2022-04-26 | 64.32.8.68 | ||||
| 2022-04-26 | 37.48.65.149 | ||||
| 2022-04-26 | 207.244.67.215 | ||||
| 2022-04-26 | 103.224.182.207 | ||||
| 2022-04-26 | 185.107.56.59 | ||||
| 2022-04-26 | 93.115.28.104 | ||||
| 2022-04-26 | 74.63.241.23 | ||||
| 2022-04-25 | 64.32.8.68 | ||||
| 2022-04-25 | 37.48.65.149 | ||||
| 2022-04-25 | 207.244.67.215 | ||||
| 2022-04-25 | 103.224.182.207 | ||||
| 2022-04-25 | 185.107.56.59 | ||||
| 2022-04-25 | 93.115.28.104 | ||||
| 2022-04-25 | 74.63.241.23 | ||||
| 2022-04-24 | 64.32.8.68 | ||||
| 2022-04-24 | 37.48.65.149 | ||||
| 2022-04-24 | 207.244.67.215 | ||||
| 2022-04-24 | 103.224.182.207 | ||||
| 2022-04-24 | 185.107.56.59 | ||||
| 2022-04-24 | 93.115.28.104 | ||||
| 2022-04-24 | 74.63.241.23 | ||||
| 2022-04-23 | 64.32.8.68 | ||||
| 2022-04-23 | 37.48.65.149 | ||||
| 2022-04-23 | 207.244.67.215 | ||||
| 2022-04-23 | 103.224.182.207 | ||||
| 2022-04-23 | 185.107.56.59 | ||||
| 2022-04-23 | 93.115.28.104 | ||||
| 2022-04-23 | 74.63.241.23 | ||||
| 2022-04-22 | 64.32.8.68 | ||||
| 2022-04-22 | 37.48.65.149 | ||||
| 2022-04-22 | 207.244.67.215 | ||||
| 2022-04-22 | 103.224.182.207 | ||||
| 2022-04-22 | 185.107.56.59 | ||||
| 2022-04-22 | 93.115.28.104 | ||||
| 2022-04-22 | 74.63.241.23 | ||||
| 2022-04-21 | 64.32.8.68 | ||||
| 2022-04-21 | 37.48.65.149 | ||||
| 2022-04-21 | 207.244.67.215 | ||||
| 2022-04-21 | 103.224.182.207 | ||||
| 2022-04-21 | 185.107.56.59 | ||||
| 2022-04-21 | 93.115.28.104 | ||||
| 2022-04-21 | 74.63.241.23 | ||||
| 2022-04-20 | 64.32.8.68 | ||||
| 2022-04-20 | 37.48.65.149 | ||||
| 2022-04-20 | 207.244.67.215 | ||||
| 2022-04-20 | 103.224.182.207 | ||||
| 2022-04-20 | 185.107.56.59 | ||||
| 2022-04-20 | 93.115.28.104 | ||||
| 2022-04-20 | 74.63.241.23 | ||||
| 2022-04-19 | 64.32.8.68 | ||||
| 2022-04-19 | 37.48.65.149 | ||||
| 2022-04-19 | 207.244.67.215 | ||||
| 2022-04-19 | 103.224.182.207 | ||||
| 2022-04-19 | 185.107.56.59 | ||||
| 2022-04-19 | 93.115.28.104 | ||||
| 2022-04-19 | 74.63.241.23 | ||||
| 2022-04-18 | 64.32.8.68 | ||||
| 2022-04-18 | 37.48.65.149 | ||||
| 2022-04-18 | 207.244.67.215 | ||||
| 2022-04-18 | 103.224.182.207 | ||||
| 2022-04-18 | 185.107.56.59 | ||||
| 2022-04-18 | 93.115.28.104 | ||||
| 2022-04-18 | 74.63.241.23 | ||||
| 2022-04-17 | 64.32.8.68 | ||||
| 2022-04-17 | 37.48.65.149 | ||||
| 2022-04-17 | 207.244.67.215 | ||||
| 2022-04-17 | 103.224.182.207 | ||||
| 2022-04-17 | 185.107.56.59 | ||||
| 2022-04-17 | 93.115.28.104 | ||||
| 2022-04-17 | 74.63.241.23 | ||||
| 2022-04-16 | 64.32.8.68 | ||||
| 2022-04-16 | 37.48.65.149 | ||||
| 2022-04-16 | 207.244.67.215 | ||||
| 2022-04-16 | 103.224.182.207 | ||||
| 2022-04-16 | 185.107.56.59 | ||||
| 2022-04-16 | 93.115.28.104 | ||||
| 2022-04-16 | 74.63.241.23 | ||||
| 2022-04-15 | 64.32.8.68 | ||||
| 2022-04-15 | 37.48.65.149 | ||||
| 2022-04-15 | 207.244.67.215 | ||||
| 2022-04-15 | 103.224.182.207 | ||||
| 2022-04-15 | 185.107.56.59 | ||||
| 2022-04-15 | 93.115.28.104 | ||||
| 2022-04-15 | 74.63.241.23 | ||||
| 2022-04-13 | 64.32.8.68 | ||||
| 2022-04-13 | 37.48.65.149 | ||||
| 2022-04-13 | 207.244.67.215 | ||||
| 2022-04-13 | 103.224.182.207 | ||||
| 2022-04-13 | 185.107.56.59 | ||||
| 2022-04-13 | 93.115.28.104 | ||||
| 2022-04-13 | 74.63.241.23 | ||||
| 2022-04-12 | 64.32.8.68 | ||||
| 2022-04-12 | 37.48.65.149 | ||||
| 2022-04-12 | 207.244.67.215 | ||||
| 2022-04-12 | 103.224.182.207 | ||||
| 2022-04-12 | 185.107.56.59 | ||||
| 2022-04-12 | 93.115.28.104 | ||||
| 2022-04-12 | 74.63.241.23 | ||||
| 2022-04-11 | 64.32.8.68 | ||||
| 2022-04-11 | 37.48.65.149 | ||||
| 2022-04-11 | 207.244.67.215 | ||||
| 2022-04-11 | 103.224.182.207 | ||||
| 2022-04-11 | 185.107.56.59 | ||||
| 2022-04-11 | 93.115.28.104 | ||||
| 2022-04-11 | 74.63.241.23 | ||||
| 2022-04-10 | 64.32.8.68 | ||||
| 2022-04-10 | 37.48.65.149 | ||||
| 2022-04-10 | 207.244.67.215 | ||||
| 2022-04-10 | 103.224.182.207 | ||||
| 2022-04-10 | 185.107.56.59 | ||||
| 2022-04-10 | 93.115.28.104 | ||||
| 2022-04-10 | 74.63.241.23 | ||||
| 2022-04-09 | 64.32.8.68 | ||||
| 2022-04-09 | 37.48.65.149 | ||||
| 2022-04-09 | 207.244.67.215 | ||||
| 2022-04-09 | 103.224.182.207 | ||||
| 2022-04-09 | 185.107.56.59 | ||||
| 2022-04-09 | 93.115.28.104 | ||||
| 2022-04-09 | 74.63.241.23 | ||||
| 2022-04-08 | 64.32.8.68 | ||||
| 2022-04-08 | 37.48.65.149 | ||||
| 2022-04-08 | 207.244.67.215 | ||||
| 2022-04-08 | 103.224.182.207 | ||||
| 2022-04-08 | 185.107.56.59 | ||||
| 2022-04-08 | 93.115.28.104 | ||||
| 2022-04-08 | 74.63.241.23 | ||||
| 2022-04-07 | 64.32.8.68 | ||||
| 2022-04-07 | 37.48.65.149 | ||||
| 2022-04-07 | 207.244.67.215 | ||||
| 2022-04-07 | 103.224.182.207 | ||||
| 2022-04-07 | 185.107.56.59 | ||||
| 2022-04-07 | 93.115.28.104 | ||||
| 2022-04-07 | 74.63.241.23 | ||||
| 2022-04-06 | 64.32.8.68 | ||||
| 2022-04-06 | 37.48.65.149 | ||||
| 2022-04-06 | 207.244.67.215 | ||||
| 2022-04-06 | 103.224.182.207 | ||||
| 2022-04-06 | 185.107.56.59 | ||||
| 2022-04-06 | 93.115.28.104 | ||||
| 2022-04-06 | 74.63.241.23 | ||||
| 2022-04-05 | 64.32.8.68 | ||||
| 2022-04-05 | 37.48.65.149 | ||||
| 2022-04-05 | 207.244.67.215 | ||||
| 2022-04-05 | 103.224.182.207 | ||||
| 2022-04-05 | 185.107.56.59 | ||||
| 2022-04-05 | 93.115.28.104 | ||||
| 2022-04-05 | 74.63.241.23 | ||||
| 2022-04-04 | 64.32.8.68 | ||||
| 2022-04-04 | 37.48.65.149 | ||||
| 2022-04-04 | 207.244.67.215 | ||||
| 2022-04-04 | 103.224.182.207 | ||||
| 2022-04-04 | 185.107.56.59 | ||||
| 2022-04-04 | 93.115.28.104 | ||||
| 2022-04-04 | 74.63.241.23 | ||||
| 2022-04-03 | 64.32.8.68 | ||||
| 2022-04-03 | 37.48.65.149 | ||||
| 2022-04-03 | 207.244.67.215 | ||||
| 2022-04-03 | 103.224.182.207 | ||||
| 2022-04-03 | 185.107.56.59 | ||||
| 2022-04-03 | 93.115.28.104 | ||||
| 2022-04-03 | 74.63.241.23 | ||||
| 2022-04-02 | 64.32.8.68 | ||||
| 2022-04-02 | 37.48.65.149 | ||||
| 2022-04-02 | 207.244.67.215 | ||||
| 2022-04-02 | 103.224.182.207 | ||||
| 2022-04-02 | 185.107.56.59 | ||||
| 2022-04-02 | 93.115.28.104 | ||||
| 2022-04-02 | 74.63.241.23 | ||||
| 2022-04-01 | 64.32.8.68 | ||||
| 2022-04-01 | 37.48.65.149 | ||||
| 2022-04-01 | 207.244.67.215 | ||||
| 2022-04-01 | 103.224.182.207 | ||||
| 2022-04-01 | 185.107.56.59 | ||||
| 2022-04-01 | 93.115.28.104 | ||||
| 2022-04-01 | 74.63.241.23 | ||||
| 2022-03-31 | 64.32.8.68 | ||||
| 2022-03-31 | 37.48.65.149 | ||||
| 2022-03-31 | 207.244.67.215 | ||||
| 2022-03-31 | 103.224.182.207 | ||||
| 2022-03-31 | 185.107.56.59 | ||||
| 2022-03-31 | 93.115.28.104 | ||||
| 2022-03-31 | 74.63.241.23 | ||||
| 2022-03-30 | 64.32.8.68 | ||||
| 2022-03-30 | 37.48.65.149 | ||||
| 2022-03-30 | 207.244.67.215 | ||||
| 2022-03-30 | 103.224.182.207 | ||||
| 2022-03-30 | 185.107.56.59 | ||||
| 2022-03-30 | 93.115.28.104 | ||||
| 2022-03-30 | 74.63.241.23 | ||||
| 2022-03-29 | 64.32.8.68 | ||||
| 2022-03-29 | 37.48.65.149 | ||||
| 2022-03-29 | 207.244.67.215 | ||||
| 2022-03-29 | 103.224.182.207 | ||||
| 2022-03-29 | 185.107.56.59 | ||||
| 2022-03-29 | 93.115.28.104 | ||||
| 2022-03-29 | 74.63.241.23 | ||||
| 2022-03-28 | 64.32.8.68 | ||||
| 2022-03-28 | 37.48.65.149 | ||||
| 2022-03-28 | 207.244.67.215 | ||||
| 2022-03-28 | 103.224.182.207 | ||||
| 2022-03-28 | 185.107.56.59 | ||||
| 2022-03-28 | 93.115.28.104 | ||||
| 2022-03-28 | 74.63.241.23 | ||||
| 2022-03-27 | 64.32.8.68 | ||||
| 2022-03-27 | 37.48.65.149 | ||||
| 2022-03-27 | 207.244.67.215 | ||||
| 2022-03-27 | 103.224.182.207 | ||||
| 2022-03-27 | 185.107.56.59 | ||||
| 2022-03-27 | 93.115.28.104 | ||||
| 2022-03-27 | 74.63.241.23 | ||||
| 2022-03-26 | 64.32.8.68 | ||||
| 2022-03-26 | 37.48.65.149 | ||||
| 2022-03-26 | 207.244.67.215 | ||||
| 2022-03-26 | 103.224.182.207 | ||||
| 2022-03-26 | 185.107.56.59 | ||||
| 2022-03-26 | 93.115.28.104 | ||||
| 2022-03-26 | 74.63.241.23 | ||||
| 2022-03-25 | 64.32.8.68 | ||||
| 2022-03-25 | 37.48.65.149 | ||||
| 2022-03-25 | 207.244.67.215 | ||||
| 2022-03-25 | 103.224.182.207 | ||||
| 2022-03-25 | 185.107.56.59 | ||||
| 2022-03-25 | 93.115.28.104 | ||||
| 2022-03-25 | 74.63.241.23 | ||||
| 2022-03-24 | 64.32.8.68 | ||||
| 2022-03-24 | 37.48.65.149 | ||||
| 2022-03-24 | 207.244.67.215 | ||||
| 2022-03-24 | 103.224.182.207 | ||||
| 2022-03-24 | 185.107.56.59 | ||||
| 2022-03-24 | 93.115.28.104 | ||||
| 2022-03-24 | 74.63.241.23 | ||||
| 2022-03-23 | 64.32.8.68 | ||||
| 2022-03-23 | 37.48.65.149 | ||||
| 2022-03-23 | 207.244.67.215 | ||||
| 2022-03-23 | 103.224.182.207 | ||||
| 2022-03-23 | 185.107.56.59 | ||||
| 2022-03-23 | 93.115.28.104 | ||||
| 2022-03-23 | 74.63.241.23 | ||||
| 2022-03-22 | 64.32.8.68 | ||||
| 2022-03-22 | 37.48.65.149 | ||||
| 2022-03-22 | 207.244.67.215 | ||||
| 2022-03-22 | 103.224.182.207 | ||||
| 2022-03-22 | 185.107.56.59 | ||||
| 2022-03-22 | 93.115.28.104 | ||||
| 2022-03-22 | 74.63.241.23 | ||||
| 2022-03-21 | 64.32.8.68 | ||||
| 2022-03-21 | 37.48.65.149 | ||||
| 2022-03-21 | 207.244.67.215 | ||||
| 2022-03-21 | 103.224.182.207 | ||||
| 2022-03-21 | 185.107.56.59 | ||||
| 2022-03-21 | 93.115.28.104 | ||||
| 2022-03-21 | 74.63.241.23 | ||||
| 2022-03-20 | 64.32.8.68 | ||||
| 2022-03-20 | 37.48.65.149 | ||||
| 2022-03-20 | 207.244.67.215 | ||||
| 2022-03-20 | 103.224.182.207 | ||||
| 2022-03-20 | 185.107.56.59 | ||||
| 2022-03-20 | 93.115.28.104 | ||||
| 2022-03-20 | 74.63.241.23 | ||||
| 2022-03-19 | 64.32.8.68 | ||||
| 2022-03-19 | 37.48.65.149 | ||||
| 2022-03-19 | 207.244.67.215 | ||||
| 2022-03-19 | 103.224.182.207 | ||||
| 2022-03-19 | 185.107.56.59 | ||||
| 2022-03-19 | 93.115.28.104 | ||||
| 2022-03-19 | 74.63.241.23 | ||||
| 2022-03-18 | 64.32.8.68 | ||||
| 2022-03-18 | 37.48.65.149 | ||||
| 2022-03-18 | 207.244.67.215 | ||||
| 2022-03-18 | 103.224.182.207 | ||||
| 2022-03-18 | 185.107.56.59 | ||||
| 2022-03-18 | 93.115.28.104 | ||||
| 2022-03-18 | 74.63.241.23 | ||||
| 2022-03-17 | 64.32.8.68 | ||||
| 2022-03-17 | 37.48.65.149 | ||||
| 2022-03-17 | 207.244.67.215 | ||||
| 2022-03-17 | 103.224.182.207 | ||||
| 2022-03-17 | 185.107.56.59 | ||||
| 2022-03-17 | 93.115.28.104 | ||||
| 2022-03-17 | 74.63.241.23 | ||||
| 2022-03-16 | 64.32.8.68 | ||||
| 2022-03-16 | 37.48.65.149 | ||||
| 2022-03-16 | 207.244.67.215 | ||||
| 2022-03-16 | 103.224.182.207 | ||||
| 2022-03-16 | 185.107.56.59 | ||||
| 2022-03-16 | 93.115.28.104 | ||||
| 2022-03-16 | 74.63.241.23 | ||||
| 2022-03-15 | 64.32.8.68 | ||||
| 2022-03-15 | 37.48.65.149 | ||||
| 2022-03-15 | 207.244.67.215 | ||||
| 2022-03-15 | 103.224.182.207 | ||||
| 2022-03-15 | 185.107.56.59 | ||||
| 2022-03-15 | 93.115.28.104 | ||||
| 2022-03-15 | 74.63.241.23 | ||||
| 2022-03-14 | 64.32.8.68 | ||||
| 2022-03-14 | 37.48.65.149 | ||||
| 2022-03-14 | 207.244.67.215 | ||||
| 2022-03-14 | 103.224.182.207 | ||||
| 2022-03-14 | 185.107.56.59 | ||||
| 2022-03-14 | 93.115.28.104 | ||||
| 2022-03-14 | 74.63.241.23 | ||||
| 2022-03-13 | 64.32.8.68 | ||||
| 2022-03-13 | 37.48.65.149 | ||||
| 2022-03-13 | 207.244.67.215 | ||||
| 2022-03-13 | 103.224.182.207 | ||||
| 2022-03-13 | 185.107.56.59 | ||||
| 2022-03-13 | 93.115.28.104 | ||||
| 2022-03-13 | 74.63.241.23 | ||||
| 2022-03-12 | 64.32.8.68 | ||||
| 2022-03-12 | 37.48.65.149 | ||||
| 2022-03-12 | 207.244.67.215 | ||||
| 2022-03-12 | 103.224.182.207 | ||||
| 2022-03-12 | 185.107.56.59 | ||||
| 2022-03-12 | 93.115.28.104 | ||||
| 2022-03-12 | 74.63.241.23 | ||||
| 2022-03-11 | 64.32.8.68 | ||||
| 2022-03-11 | 37.48.65.149 | ||||
| 2022-03-11 | 207.244.67.215 | ||||
| 2022-03-11 | 103.224.182.207 | ||||
| 2022-03-11 | 185.107.56.59 | ||||
| 2022-03-11 | 93.115.28.104 | ||||
| 2022-03-11 | 74.63.241.23 | ||||
| 2022-03-10 | 64.32.8.68 | ||||
| 2022-03-10 | 37.48.65.149 | ||||
| 2022-03-10 | 207.244.67.215 | ||||
| 2022-03-10 | 103.224.182.207 | ||||
| 2022-03-10 | 185.107.56.59 | ||||
| 2022-03-10 | 93.115.28.104 | ||||
| 2022-03-10 | 74.63.241.23 | ||||
| 2022-03-09 | 64.32.8.68 | ||||
| 2022-03-09 | 37.48.65.149 | ||||
| 2022-03-09 | 207.244.67.215 | ||||
| 2022-03-09 | 103.224.182.207 | ||||
| 2022-03-09 | 185.107.56.59 | ||||
| 2022-03-09 | 93.115.28.104 | ||||
| 2022-03-09 | 74.63.241.23 | ||||
| 2022-03-08 | 64.32.8.68 | ||||
| 2022-03-08 | 37.48.65.149 | ||||
| 2022-03-08 | 207.244.67.215 | ||||
| 2022-03-08 | 103.224.182.207 | ||||
| 2022-03-08 | 185.107.56.59 | ||||
| 2022-03-08 | 93.115.28.104 | ||||
| 2022-03-08 | 74.63.241.23 | ||||
| 2022-03-07 | 64.32.8.68 | ||||
| 2022-03-07 | 37.48.65.149 | ||||
| 2022-03-07 | 207.244.67.215 | ||||
| 2022-03-07 | 103.224.182.207 | ||||
| 2022-03-07 | 185.107.56.59 | ||||
| 2022-03-07 | 93.115.28.104 | ||||
| 2022-03-07 | 74.63.241.23 | ||||
| 2022-03-06 | 64.32.8.68 | ||||
| 2022-03-06 | 37.48.65.149 | ||||
| 2022-03-06 | 207.244.67.215 | ||||
| 2022-03-06 | 103.224.182.207 | ||||
| 2022-03-06 | 185.107.56.59 | ||||
| 2022-03-06 | 93.115.28.104 | ||||
| 2022-03-06 | 74.63.241.23 | ||||
| 2022-03-05 | 64.32.8.68 | ||||
| 2022-03-05 | 37.48.65.149 | ||||
| 2022-03-05 | 207.244.67.215 | ||||
| 2022-03-05 | 103.224.182.207 | ||||
| 2022-03-05 | 185.107.56.59 | ||||
| 2022-03-05 | 93.115.28.104 | ||||
| 2022-03-05 | 74.63.241.23 | ||||
| 2022-03-04 | 64.32.8.68 | ||||
| 2022-03-04 | 37.48.65.149 | ||||
| 2022-03-04 | 207.244.67.215 | ||||
| 2022-03-04 | 103.224.182.207 | ||||
| 2022-03-04 | 185.107.56.59 | ||||
| 2022-03-04 | 93.115.28.104 | ||||
| 2022-03-04 | 74.63.241.23 | ||||
| 2022-03-03 | 64.32.8.68 | ||||
| 2022-03-03 | 37.48.65.149 | ||||
| 2022-03-03 | 207.244.67.215 | ||||
| 2022-03-03 | 103.224.182.207 | ||||
| 2022-03-03 | 185.107.56.59 | ||||
| 2022-03-03 | 93.115.28.104 | ||||
| 2022-03-03 | 74.63.241.23 | ||||
| 2022-03-02 | 64.32.8.68 | ||||
| 2022-03-02 | 37.48.65.149 | ||||
| 2022-03-02 | 207.244.67.215 | ||||
| 2022-03-02 | 103.224.182.207 | ||||
| 2022-03-02 | 185.107.56.59 | ||||
| 2022-03-02 | 93.115.28.104 | ||||
| 2022-03-02 | 74.63.241.23 | ||||
| 2022-03-01 | 64.32.8.68 | ||||
| 2022-03-01 | 37.48.65.149 | ||||
| 2022-03-01 | 207.244.67.215 | ||||
| 2022-03-01 | 103.224.182.207 | ||||
| 2022-03-01 | 185.107.56.59 | ||||
| 2022-03-01 | 93.115.28.104 | ||||
| 2022-03-01 | 74.63.241.23 | ||||
| 2022-02-28 | 64.32.8.68 | ||||
| 2022-02-28 | 37.48.65.149 | ||||
| 2022-02-28 | 207.244.67.215 | ||||
| 2022-02-28 | 103.224.182.207 | ||||
| 2022-02-28 | 185.107.56.59 | ||||
| 2022-02-28 | 93.115.28.104 | ||||
| 2022-02-28 | 74.63.241.23 | ||||
| 2022-02-27 | 64.32.8.68 | ||||
| 2022-02-27 | 37.48.65.149 | ||||
| 2022-02-27 | 207.244.67.215 | ||||
| 2022-02-27 | 103.224.182.207 | ||||
| 2022-02-27 | 185.107.56.59 | ||||
| 2022-02-27 | 93.115.28.104 | ||||
| 2022-02-27 | 74.63.241.23 | ||||
| 2022-02-26 | 64.32.8.68 | ||||
| 2022-02-26 | 37.48.65.149 | ||||
| 2022-02-26 | 207.244.67.215 | ||||
| 2022-02-26 | 103.224.182.207 | ||||
| 2022-02-26 | 185.107.56.59 | ||||
| 2022-02-26 | 93.115.28.104 | ||||
| 2022-02-26 | 74.63.241.23 | ||||
| 2022-02-25 | 64.32.8.68 | ||||
| 2022-02-25 | 37.48.65.149 | ||||
| 2022-02-25 | 207.244.67.215 | ||||
| 2022-02-25 | 103.224.182.207 | ||||
| 2022-02-25 | 185.107.56.59 | ||||
| 2022-02-25 | 93.115.28.104 | ||||
| 2022-02-25 | 74.63.241.23 | ||||
| 2022-02-24 | 64.32.8.68 | ||||
| 2022-02-24 | 37.48.65.149 | ||||
| 2022-02-24 | 207.244.67.215 | ||||
| 2022-02-24 | 103.224.182.207 | ||||
| 2022-02-24 | 185.107.56.59 | ||||
| 2022-02-24 | 93.115.28.104 | ||||
| 2022-02-24 | 74.63.241.23 | ||||
| 2022-02-23 | 64.32.8.68 | ||||
| 2022-02-23 | 37.48.65.149 | ||||
| 2022-02-23 | 207.244.67.215 | ||||
| 2022-02-23 | 103.224.182.207 | ||||
| 2022-02-23 | 185.107.56.59 | ||||
| 2022-02-23 | 93.115.28.104 | ||||
| 2022-02-23 | 74.63.241.23 | ||||
| 2022-02-22 | 64.32.8.68 | ||||
| 2022-02-22 | 37.48.65.149 | ||||
| 2022-02-22 | 207.244.67.215 | ||||
| 2022-02-22 | 103.224.182.207 | ||||
| 2022-02-22 | 185.107.56.59 | ||||
| 2022-02-22 | 93.115.28.104 | ||||
| 2022-02-22 | 74.63.241.23 | ||||
| 2022-02-21 | 64.32.8.68 | ||||
| 2022-02-21 | 37.48.65.149 | ||||
| 2022-02-21 | 207.244.67.215 | ||||
| 2022-02-21 | 103.224.182.207 | ||||
| 2022-02-21 | 185.107.56.59 | ||||
| 2022-02-21 | 93.115.28.104 | ||||
| 2022-02-21 | 74.63.241.23 | ||||
| 2022-02-20 | 64.32.8.68 | ||||
| 2022-02-20 | 37.48.65.149 | ||||
| 2022-02-20 | 207.244.67.215 | ||||
| 2022-02-20 | 103.224.182.207 | ||||
| 2022-02-20 | 185.107.56.59 | ||||
| 2022-02-20 | 93.115.28.104 | ||||
| 2022-02-20 | 74.63.241.23 | ||||
| 2022-02-19 | 64.32.8.68 | ||||
| 2022-02-19 | 37.48.65.149 | ||||
| 2022-02-19 | 207.244.67.215 | ||||
| 2022-02-19 | 103.224.182.207 | ||||
| 2022-02-19 | 185.107.56.59 | ||||
| 2022-02-19 | 93.115.28.104 | ||||
| 2022-02-19 | 74.63.241.23 | ||||
| 2022-02-18 | 64.32.8.68 | ||||
| 2022-02-18 | 37.48.65.149 | ||||
| 2022-02-18 | 207.244.67.215 | ||||
| 2022-02-18 | 103.224.182.207 | ||||
| 2022-02-18 | 185.107.56.59 | ||||
| 2022-02-18 | 93.115.28.104 | ||||
| 2022-02-18 | 74.63.241.23 | ||||
| 2022-02-17 | 64.32.8.68 | ||||
| 2022-02-17 | 37.48.65.149 | ||||
| 2022-02-17 | 207.244.67.215 | ||||
| 2022-02-17 | 103.224.182.207 | ||||
| 2022-02-17 | 185.107.56.59 | ||||
| 2022-02-17 | 93.115.28.104 | ||||
| 2022-02-17 | 74.63.241.23 | ||||
| 2022-02-16 | 64.32.8.68 | ||||
| 2022-02-16 | 37.48.65.149 | ||||
| 2022-02-16 | 207.244.67.215 | ||||
| 2022-02-16 | 103.224.182.207 | ||||
| 2022-02-16 | 185.107.56.59 | ||||
| 2022-02-16 | 93.115.28.104 | ||||
| 2022-02-16 | 74.63.241.23 | ||||
| 2022-02-15 | 64.32.8.68 | ||||
| 2022-02-15 | 37.48.65.149 | ||||
| 2022-02-15 | 207.244.67.215 | ||||
| 2022-02-15 | 103.224.182.207 | ||||
| 2022-02-15 | 185.107.56.59 | ||||
| 2022-02-15 | 93.115.28.104 | ||||
| 2022-02-15 | 74.63.241.23 | ||||
| 2022-02-14 | 64.32.8.68 | ||||
| 2022-02-14 | 37.48.65.149 | ||||
| 2022-02-14 | 207.244.67.215 | ||||
| 2022-02-14 | 103.224.182.207 | ||||
| 2022-02-14 | 185.107.56.59 | ||||
| 2022-02-14 | 93.115.28.104 | ||||
| 2022-02-14 | 74.63.241.23 | ||||
| 2022-02-13 | 64.32.8.68 | ||||
| 2022-02-13 | 37.48.65.149 | ||||
| 2022-02-13 | 207.244.67.215 | ||||
| 2022-02-13 | 103.224.182.207 | ||||
| 2022-02-13 | 185.107.56.59 | ||||
| 2022-02-13 | 93.115.28.104 | ||||
| 2022-02-13 | 74.63.241.23 | ||||
| 2022-02-12 | 64.32.8.68 | ||||
| 2022-02-12 | 37.48.65.149 | ||||
| 2022-02-12 | 207.244.67.215 | ||||
| 2022-02-12 | 103.224.182.207 | ||||
| 2022-02-12 | 185.107.56.59 | ||||
| 2022-02-12 | 93.115.28.104 | ||||
| 2022-02-12 | 74.63.241.23 | ||||
| 2022-02-11 | 64.32.8.68 | ||||
| 2022-02-11 | 37.48.65.149 | ||||
| 2022-02-11 | 207.244.67.215 | ||||
| 2022-02-11 | 103.224.182.207 | ||||
| 2022-02-11 | 185.107.56.59 | ||||
| 2022-02-11 | 93.115.28.104 | ||||
| 2022-02-11 | 74.63.241.23 | ||||
| 2022-02-10 | 64.32.8.68 | ||||
| 2022-02-10 | 37.48.65.149 | ||||
| 2022-02-10 | 207.244.67.215 | ||||
| 2022-02-10 | 103.224.182.207 | ||||
| 2022-02-10 | 185.107.56.59 | ||||
| 2022-02-10 | 93.115.28.104 | ||||
| 2022-02-10 | 74.63.241.23 | ||||
| 2022-02-09 | 64.32.8.68 | ||||
| 2022-02-09 | 37.48.65.149 | ||||
| 2022-02-09 | 207.244.67.215 | ||||
| 2022-02-09 | 103.224.182.207 | ||||
| 2022-02-09 | 185.107.56.59 | ||||
| 2022-02-09 | 93.115.28.104 | ||||
| 2022-02-09 | 74.63.241.23 | ||||
| 2022-02-08 | 64.32.8.68 | ||||
| 2022-02-08 | 37.48.65.149 | ||||
| 2022-02-08 | 207.244.67.215 | ||||
| 2022-02-08 | 103.224.182.207 | ||||
| 2022-02-08 | 185.107.56.59 | ||||
| 2022-02-08 | 93.115.28.104 | ||||
| 2022-02-08 | 74.63.241.23 | ||||
| 2022-02-07 | 64.32.8.68 | ||||
| 2022-02-07 | 37.48.65.149 | ||||
| 2022-02-07 | 207.244.67.215 | ||||
| 2022-02-07 | 103.224.182.207 | ||||
| 2022-02-07 | 185.107.56.59 | ||||
| 2022-02-07 | 93.115.28.104 | ||||
| 2022-02-07 | 74.63.241.23 | ||||
| 2022-02-06 | 64.32.8.68 | ||||
| 2022-02-06 | 37.48.65.149 | ||||
| 2022-02-06 | 207.244.67.215 | ||||
| 2022-02-06 | 103.224.182.207 | ||||
| 2022-02-06 | 185.107.56.59 | ||||
| 2022-02-06 | 93.115.28.104 | ||||
| 2022-02-06 | 74.63.241.23 | ||||
| 2022-02-05 | 64.32.8.68 | ||||
| 2022-02-05 | 37.48.65.149 | ||||
| 2022-02-05 | 207.244.67.215 | ||||
| 2022-02-05 | 103.224.182.207 | ||||
| 2022-02-05 | 185.107.56.59 | ||||
| 2022-02-05 | 93.115.28.104 | ||||
| 2022-02-05 | 74.63.241.23 | ||||
| 2022-02-04 | 64.32.8.68 | ||||
| 2022-02-04 | 37.48.65.149 | ||||
| 2022-02-04 | 207.244.67.215 | ||||
| 2022-02-04 | 103.224.182.207 | ||||
| 2022-02-04 | 185.107.56.59 | ||||
| 2022-02-04 | 93.115.28.104 | ||||
| 2022-02-04 | 74.63.241.23 | ||||
| 2022-02-03 | 64.32.8.68 | ||||
| 2022-02-03 | 37.48.65.149 | ||||
| 2022-02-03 | 207.244.67.215 | ||||
| 2022-02-03 | 103.224.182.207 | ||||
| 2022-02-03 | 185.107.56.59 | ||||
| 2022-02-03 | 93.115.28.104 | ||||
| 2022-02-03 | 74.63.241.23 | ||||
| 2022-02-02 | 64.32.8.68 | ||||
| 2022-02-02 | 37.48.65.149 | ||||
| 2022-02-02 | 207.244.67.215 | ||||
| 2022-02-02 | 103.224.182.207 | ||||
| 2022-02-02 | 185.107.56.59 | ||||
| 2022-02-02 | 93.115.28.104 | ||||
| 2022-02-02 | 74.63.241.23 | ||||
| 2022-02-01 | 64.32.8.68 | ||||
| 2022-02-01 | 37.48.65.149 | ||||
| 2022-02-01 | 207.244.67.215 | ||||
| 2022-02-01 | 103.224.182.207 | ||||
| 2022-02-01 | 185.107.56.59 | ||||
| 2022-02-01 | 93.115.28.104 | ||||
| 2022-02-01 | 74.63.241.23 | ||||
| 2022-01-31 | 64.32.8.68 | ||||
| 2022-01-31 | 37.48.65.149 | ||||
| 2022-01-31 | 207.244.67.215 | ||||
| 2022-01-31 | 103.224.182.207 | ||||
| 2022-01-31 | 185.107.56.59 | ||||
| 2022-01-31 | 93.115.28.104 | ||||
| 2022-01-31 | 74.63.241.23 | ||||
| 2022-01-30 | 64.32.8.68 | ||||
| 2022-01-30 | 37.48.65.149 | ||||
| 2022-01-30 | 207.244.67.215 | ||||
| 2022-01-30 | 103.224.182.207 | ||||
| 2022-01-30 | 185.107.56.59 | ||||
| 2022-01-30 | 93.115.28.104 | ||||
| 2022-01-30 | 74.63.241.23 | ||||
| 2022-01-29 | 64.32.8.68 | ||||
| 2022-01-29 | 37.48.65.149 | ||||
| 2022-01-29 | 207.244.67.215 | ||||
| 2022-01-29 | 103.224.182.207 | ||||
| 2022-01-29 | 185.107.56.59 | ||||
| 2022-01-29 | 93.115.28.104 | ||||
| 2022-01-29 | 74.63.241.23 | ||||
| 2022-01-28 | 64.32.8.68 | ||||
| 2022-01-28 | 37.48.65.149 | ||||
| 2022-01-28 | 207.244.67.215 | ||||
| 2022-01-28 | 103.224.182.207 | ||||
| 2022-01-28 | 185.107.56.59 | ||||
| 2022-01-28 | 93.115.28.104 | ||||
| 2022-01-28 | 74.63.241.23 | ||||
| 2022-01-27 | 64.32.8.68 | ||||
| 2022-01-27 | 37.48.65.149 | ||||
| 2022-01-27 | 207.244.67.215 | ||||
| 2022-01-27 | 103.224.182.207 | ||||
| 2022-01-27 | 185.107.56.59 | ||||
| 2022-01-27 | 93.115.28.104 | ||||
| 2022-01-27 | 74.63.241.23 | ||||
| 2022-01-26 | 64.32.8.68 | ||||
| 2022-01-26 | 37.48.65.149 | ||||
| 2022-01-26 | 207.244.67.215 | ||||
| 2022-01-26 | 103.224.182.207 | ||||
| 2022-01-26 | 185.107.56.59 | ||||
| 2022-01-26 | 93.115.28.104 | ||||
| 2022-01-26 | 74.63.241.23 | ||||
| 2022-01-25 | 64.32.8.68 | ||||
| 2022-01-25 | 37.48.65.149 | ||||
| 2022-01-25 | 207.244.67.215 | ||||
| 2022-01-25 | 103.224.182.207 | ||||
| 2022-01-25 | 185.107.56.59 | ||||
| 2022-01-25 | 93.115.28.104 | ||||
| 2022-01-25 | 74.63.241.23 | ||||
| 2022-01-24 | 64.32.8.68 | ||||
| 2022-01-24 | 37.48.65.149 | ||||
| 2022-01-24 | 207.244.67.215 | ||||
| 2022-01-24 | 103.224.182.207 | ||||
| 2022-01-24 | 185.107.56.59 | ||||
| 2022-01-24 | 93.115.28.104 | ||||
| 2022-01-24 | 74.63.241.23 | ||||
| 2022-01-23 | 64.32.8.68 | ||||
| 2022-01-23 | 37.48.65.149 | ||||
| 2022-01-23 | 207.244.67.215 | ||||
| 2022-01-23 | 103.224.182.207 | ||||
| 2022-01-23 | 185.107.56.59 | ||||
| 2022-01-23 | 93.115.28.104 | ||||
| 2022-01-23 | 74.63.241.23 | ||||
| 2022-01-22 | 64.32.8.68 | ||||
| 2022-01-22 | 37.48.65.149 | ||||
| 2022-01-22 | 207.244.67.215 | ||||
| 2022-01-22 | 103.224.182.207 | ||||
| 2022-01-22 | 185.107.56.59 | ||||
| 2022-01-22 | 93.115.28.104 | ||||
| 2022-01-22 | 74.63.241.23 | ||||
| 2022-01-21 | 64.32.8.68 | ||||
| 2022-01-21 | 37.48.65.149 | ||||
| 2022-01-21 | 207.244.67.215 | ||||
| 2022-01-21 | 103.224.182.207 | ||||
| 2022-01-21 | 185.107.56.59 | ||||
| 2022-01-21 | 93.115.28.104 | ||||
| 2022-01-21 | 74.63.241.23 | ||||
| 2022-01-20 | 64.32.8.68 | ||||
| 2022-01-20 | 37.48.65.149 | ||||
| 2022-01-20 | 207.244.67.215 | ||||
| 2022-01-20 | 103.224.182.207 | ||||
| 2022-01-20 | 185.107.56.59 | ||||
| 2022-01-20 | 93.115.28.104 | ||||
| 2022-01-20 | 74.63.241.23 | ||||
| 2022-01-19 | 64.32.8.68 | ||||
| 2022-01-19 | 37.48.65.149 | ||||
| 2022-01-19 | 207.244.67.215 | ||||
| 2022-01-19 | 103.224.182.207 | ||||
| 2022-01-19 | 185.107.56.59 | ||||
| 2022-01-19 | 93.115.28.104 | ||||
| 2022-01-19 | 74.63.241.23 | ||||
| 2022-01-18 | 64.32.8.68 | ||||
| 2022-01-18 | 37.48.65.149 | ||||
| 2022-01-18 | 207.244.67.215 | ||||
| 2022-01-18 | 103.224.182.207 | ||||
| 2022-01-18 | 185.107.56.59 | ||||
| 2022-01-18 | 93.115.28.104 | ||||
| 2022-01-18 | 74.63.241.23 | ||||
| 2022-01-17 | 64.32.8.68 | ||||
| 2022-01-17 | 37.48.65.149 | ||||
| 2022-01-17 | 207.244.67.215 | ||||
| 2022-01-17 | 103.224.182.207 | ||||
| 2022-01-17 | 185.107.56.59 | ||||
| 2022-01-17 | 93.115.28.104 | ||||
| 2022-01-17 | 74.63.241.23 | ||||
| 2022-01-16 | 64.32.8.68 | ||||
| 2022-01-16 | 37.48.65.149 | ||||
| 2022-01-16 | 207.244.67.215 | ||||
| 2022-01-16 | 103.224.182.207 | ||||
| 2022-01-16 | 185.107.56.59 | ||||
| 2022-01-16 | 93.115.28.104 | ||||
| 2022-01-16 | 74.63.241.23 | ||||
| 2022-01-15 | 64.32.8.68 | ||||
| 2022-01-15 | 37.48.65.149 | ||||
| 2022-01-15 | 207.244.67.215 | ||||
| 2022-01-15 | 103.224.182.207 | ||||
| 2022-01-15 | 185.107.56.59 | ||||
| 2022-01-15 | 93.115.28.104 | ||||
| 2022-01-15 | 74.63.241.23 | ||||
| 2022-01-14 | 64.32.8.68 | ||||
| 2022-01-14 | 37.48.65.149 | ||||
| 2022-01-14 | 207.244.67.215 | ||||
| 2022-01-14 | 103.224.182.207 | ||||
| 2022-01-14 | 185.107.56.59 | ||||
| 2022-01-14 | 93.115.28.104 | ||||
| 2022-01-14 | 74.63.241.23 | ||||
| 2022-01-13 | 64.32.8.68 | ||||
| 2022-01-13 | 37.48.65.149 | ||||
| 2022-01-13 | 207.244.67.215 | ||||
| 2022-01-13 | 103.224.182.207 | ||||
| 2022-01-13 | 185.107.56.59 | ||||
| 2022-01-13 | 93.115.28.104 | ||||
| 2022-01-13 | 74.63.241.23 | ||||
| 2022-01-12 | 64.32.8.68 | ||||
| 2022-01-12 | 37.48.65.149 | ||||
| 2022-01-12 | 207.244.67.215 | ||||
| 2022-01-12 | 103.224.182.207 | ||||
| 2022-01-12 | 185.107.56.59 | ||||
| 2022-01-12 | 93.115.28.104 | ||||
| 2022-01-12 | 74.63.241.23 | ||||
| 2022-01-11 | 64.32.8.68 | ||||
| 2022-01-11 | 37.48.65.149 | ||||
| 2022-01-11 | 207.244.67.215 | ||||
| 2022-01-11 | 103.224.182.207 | ||||
| 2022-01-11 | 185.107.56.59 | ||||
| 2022-01-11 | 93.115.28.104 | ||||
| 2022-01-11 | 74.63.241.23 | ||||
| 2022-01-10 | 64.32.8.68 | ||||
| 2022-01-10 | 37.48.65.149 | ||||
| 2022-01-10 | 207.244.67.215 | ||||
| 2022-01-10 | 103.224.182.207 | ||||
| 2022-01-10 | 185.107.56.59 | ||||
| 2022-01-10 | 93.115.28.104 | ||||
| 2022-01-10 | 74.63.241.23 | ||||
| 2022-01-09 | 64.32.8.68 | ||||
| 2022-01-09 | 37.48.65.149 | ||||
| 2022-01-09 | 207.244.67.215 | ||||
| 2022-01-09 | 103.224.182.207 | ||||
| 2022-01-09 | 185.107.56.59 | ||||
| 2022-01-09 | 93.115.28.104 | ||||
| 2022-01-09 | 74.63.241.23 | ||||
| 2022-01-08 | 64.32.8.68 | ||||
| 2022-01-08 | 37.48.65.149 | ||||
| 2022-01-08 | 207.244.67.215 | ||||
| 2022-01-08 | 103.224.182.207 | ||||
| 2022-01-08 | 185.107.56.59 | ||||
| 2022-01-08 | 93.115.28.104 | ||||
| 2022-01-08 | 74.63.241.23 | ||||
| 2022-01-07 | 64.32.8.68 | ||||
| 2022-01-07 | 37.48.65.149 | ||||
| 2022-01-07 | 207.244.67.215 | ||||
| 2022-01-07 | 103.224.182.207 | ||||
| 2022-01-07 | 185.107.56.59 | ||||
| 2022-01-07 | 93.115.28.104 | ||||
| 2022-01-07 | 74.63.241.23 | ||||
| 2022-01-06 | 64.32.8.68 | ||||
| 2022-01-06 | 37.48.65.149 | ||||
| 2022-01-06 | 207.244.67.215 | ||||
| 2022-01-06 | 103.224.182.207 | ||||
| 2022-01-06 | 185.107.56.59 | ||||
| 2022-01-06 | 93.115.28.104 | ||||
| 2022-01-06 | 74.63.241.23 | ||||
| 2021-12-28 | 64.32.8.68 | ||||
| 2021-12-28 | 37.48.65.149 | ||||
| 2021-12-28 | 207.244.67.215 | ||||
| 2021-12-28 | 103.224.182.207 | ||||
| 2021-12-28 | 185.107.56.59 | ||||
| 2021-12-28 | 93.115.28.104 | ||||
| 2021-12-28 | 74.63.241.23 | ||||
| 2021-12-27 | 64.32.8.68 | ||||
| 2021-12-27 | 37.48.65.149 | ||||
| 2021-12-27 | 207.244.67.215 | ||||
| 2021-12-27 | 103.224.182.207 | ||||
| 2021-12-27 | 185.107.56.59 | ||||
| 2021-12-27 | 93.115.28.104 | ||||
| 2021-12-27 | 74.63.241.23 | ||||
| 2021-12-26 | 64.32.8.68 | ||||
| 2021-12-26 | 37.48.65.149 | ||||
| 2021-12-26 | 207.244.67.215 | ||||
| 2021-12-26 | 103.224.182.207 | ||||
| 2021-12-26 | 185.107.56.59 | ||||
| 2021-12-26 | 93.115.28.104 | ||||
| 2021-12-26 | 74.63.241.23 | ||||
| 2021-12-25 | 64.32.8.68 | ||||
| 2021-12-25 | 37.48.65.149 | ||||
| 2021-12-25 | 207.244.67.215 | ||||
| 2021-12-25 | 103.224.182.207 | ||||
| 2021-12-25 | 185.107.56.59 | ||||
| 2021-12-25 | 93.115.28.104 | ||||
| 2021-12-25 | 74.63.241.23 | ||||
| 2021-12-24 | 64.32.8.68 | ||||
| 2021-12-24 | 37.48.65.149 | ||||
| 2021-12-24 | 207.244.67.215 | ||||
| 2021-12-24 | 103.224.182.207 | ||||
| 2021-12-24 | 185.107.56.59 | ||||
| 2021-12-24 | 93.115.28.104 | ||||
| 2021-12-24 | 74.63.241.23 | ||||
| 2021-12-23 | 64.32.8.68 | ||||
| 2021-12-23 | 37.48.65.149 | ||||
| 2021-12-23 | 207.244.67.215 | ||||
| 2021-12-23 | 103.224.182.207 | ||||
| 2021-12-23 | 185.107.56.59 | ||||
| 2021-12-23 | 93.115.28.104 | ||||
| 2021-12-23 | 74.63.241.23 | ||||
| 2021-12-22 | 64.32.8.68 | ||||
| 2021-12-22 | 37.48.65.149 | ||||
| 2021-12-22 | 207.244.67.215 | ||||
| 2021-12-22 | 103.224.182.207 | ||||
| 2021-12-22 | 185.107.56.59 | ||||
| 2021-12-22 | 93.115.28.104 | ||||
| 2021-12-22 | 74.63.241.23 | ||||
| 2021-12-21 | 64.32.8.68 | ||||
| 2021-12-21 | 37.48.65.149 | ||||
| 2021-12-21 | 207.244.67.215 | ||||
| 2021-12-21 | 103.224.182.207 | ||||
| 2021-12-21 | 185.107.56.59 | ||||
| 2021-12-21 | 93.115.28.104 | ||||
| 2021-12-21 | 74.63.241.23 | ||||
| 2021-12-20 | 64.32.8.68 | ||||
| 2021-12-20 | 37.48.65.149 | ||||
| 2021-12-20 | 207.244.67.215 | ||||
| 2021-12-20 | 103.224.182.207 | ||||
| 2021-12-20 | 185.107.56.59 | ||||
| 2021-12-20 | 93.115.28.104 | ||||
| 2021-12-20 | 74.63.241.23 | ||||
| 2021-12-19 | 64.32.8.68 | ||||
| 2021-12-19 | 37.48.65.149 | ||||
| 2021-12-19 | 207.244.67.215 | ||||
| 2021-12-19 | 103.224.182.207 | ||||
| 2021-12-19 | 185.107.56.59 | ||||
| 2021-12-19 | 93.115.28.104 | ||||
| 2021-12-19 | 74.63.241.23 | ||||
| 2021-12-18 | 64.32.8.68 | ||||
| 2021-12-18 | 37.48.65.149 | ||||
| 2021-12-18 | 207.244.67.215 | ||||
| 2021-12-18 | 103.224.182.207 | ||||
| 2021-12-18 | 185.107.56.59 | ||||
| 2021-12-18 | 93.115.28.104 | ||||
| 2021-12-18 | 74.63.241.23 | ||||
| 2021-12-17 | 64.32.8.68 | ||||
| 2021-12-17 | 37.48.65.149 | ||||
| 2021-12-17 | 207.244.67.215 | ||||
| 2021-12-17 | 103.224.182.207 | ||||
| 2021-12-17 | 185.107.56.59 | ||||
| 2021-12-17 | 93.115.28.104 | ||||
| 2021-12-17 | 74.63.241.23 | ||||
| 2021-12-16 | 64.32.8.68 | ||||
| 2021-12-16 | 37.48.65.149 | ||||
| 2021-12-16 | 207.244.67.215 | ||||
| 2021-12-16 | 103.224.182.207 | ||||
| 2021-12-16 | 185.107.56.59 | ||||
| 2021-12-16 | 93.115.28.104 | ||||
| 2021-12-16 | 74.63.241.23 | ||||
| 2021-12-15 | 64.32.8.68 | ||||
| 2021-12-15 | 37.48.65.149 | ||||
| 2021-12-15 | 207.244.67.215 | ||||
| 2021-12-15 | 103.224.182.207 | ||||
| 2021-12-15 | 185.107.56.59 | ||||
| 2021-12-15 | 93.115.28.104 | ||||
| 2021-12-15 | 74.63.241.23 | ||||
| 2021-12-14 | 64.32.8.68 | ||||
| 2021-12-14 | 37.48.65.149 | ||||
| 2021-12-14 | 207.244.67.215 | ||||
| 2021-12-14 | 103.224.182.207 | ||||
| 2021-12-14 | 185.107.56.59 | ||||
| 2021-12-14 | 93.115.28.104 | ||||
| 2021-12-14 | 74.63.241.23 | ||||
| 2021-12-13 | 64.32.8.68 | ||||
| 2021-12-13 | 37.48.65.149 | ||||
| 2021-12-13 | 207.244.67.215 | ||||
| 2021-12-13 | 103.224.182.207 | ||||
| 2021-12-13 | 185.107.56.59 | ||||
| 2021-12-13 | 93.115.28.104 | ||||
| 2021-12-13 | 74.63.241.23 | ||||
| 2021-12-12 | 64.32.8.68 | ||||
| 2021-12-12 | 37.48.65.149 | ||||
| 2021-12-12 | 207.244.67.215 | ||||
| 2021-12-12 | 103.224.182.207 | ||||
| 2021-12-12 | 185.107.56.59 | ||||
| 2021-12-12 | 93.115.28.104 | ||||
| 2021-12-12 | 74.63.241.23 | ||||
| 2021-12-11 | 64.32.8.68 | ||||
| 2021-12-11 | 37.48.65.149 | ||||
| 2021-12-11 | 207.244.67.215 | ||||
| 2021-12-11 | 103.224.182.207 | ||||
| 2021-12-11 | 185.107.56.59 | ||||
| 2021-12-11 | 93.115.28.104 | ||||
| 2021-12-11 | 74.63.241.23 | ||||
| 2021-12-10 | 64.32.8.68 | ||||
| 2021-12-10 | 37.48.65.149 | ||||
| 2021-12-10 | 207.244.67.215 | ||||
| 2021-12-10 | 103.224.182.207 | ||||
| 2021-12-10 | 185.107.56.59 | ||||
| 2021-12-10 | 93.115.28.104 | ||||
| 2021-12-10 | 74.63.241.23 | ||||
| 2021-12-09 | 64.32.8.68 | ||||
| 2021-12-09 | 37.48.65.149 | ||||
| 2021-12-09 | 207.244.67.215 | ||||
| 2021-12-09 | 103.224.182.207 | ||||
| 2021-12-09 | 185.107.56.59 | ||||
| 2021-12-09 | 93.115.28.104 | ||||
| 2021-12-09 | 74.63.241.23 | ||||
| 2021-12-08 | 64.32.8.68 | ||||
| 2021-12-08 | 37.48.65.149 | ||||
| 2021-12-08 | 207.244.67.215 | ||||
| 2021-12-08 | 103.224.182.207 | ||||
| 2021-12-08 | 185.107.56.59 | ||||
| 2021-12-08 | 93.115.28.104 | ||||
| 2021-12-08 | 74.63.241.23 | ||||
| 2021-12-07 | 64.32.8.68 | ||||
| 2021-12-07 | 37.48.65.149 | ||||
| 2021-12-07 | 207.244.67.215 | ||||
| 2021-12-07 | 103.224.182.207 | ||||
| 2021-12-07 | 185.107.56.59 | ||||
| 2021-12-07 | 93.115.28.104 | ||||
| 2021-12-07 | 74.63.241.23 | ||||
| 2021-12-06 | 64.32.8.68 | ||||
| 2021-12-06 | 37.48.65.149 | ||||
| 2021-12-06 | 207.244.67.215 | ||||
| 2021-12-06 | 103.224.182.207 | ||||
| 2021-12-06 | 185.107.56.59 | ||||
| 2021-12-06 | 93.115.28.104 | ||||
| 2021-12-06 | 74.63.241.23 | ||||
| 2021-12-05 | 64.32.8.68 | ||||
| 2021-12-05 | 37.48.65.149 | ||||
| 2021-12-05 | 207.244.67.215 | ||||
| 2021-12-05 | 103.224.182.207 | ||||
| 2021-12-05 | 185.107.56.59 | ||||
| 2021-12-05 | 93.115.28.104 | ||||
| 2021-12-05 | 74.63.241.23 | ||||
| 2021-12-04 | 64.32.8.68 | ||||
| 2021-12-04 | 37.48.65.149 | ||||
| 2021-12-04 | 207.244.67.215 | ||||
| 2021-12-04 | 103.224.182.207 | ||||
| 2021-12-04 | 185.107.56.59 | ||||
| 2021-12-04 | 93.115.28.104 | ||||
| 2021-12-04 | 74.63.241.23 | ||||
| 2021-12-03 | 64.32.8.68 | ||||
| 2021-12-03 | 37.48.65.149 | ||||
| 2021-12-03 | 207.244.67.215 | ||||
| 2021-12-03 | 103.224.182.207 | ||||
| 2021-12-03 | 185.107.56.59 | ||||
| 2021-12-03 | 93.115.28.104 | ||||
| 2021-12-03 | 74.63.241.23 | ||||
| 2021-12-02 | 64.32.8.68 | ||||
| 2021-12-02 | 37.48.65.149 | ||||
| 2021-12-02 | 207.244.67.215 | ||||
| 2021-12-02 | 103.224.182.207 | ||||
| 2021-12-02 | 185.107.56.59 | ||||
| 2021-12-02 | 93.115.28.104 | ||||
| 2021-12-02 | 74.63.241.23 | ||||
| 2021-12-01 | 64.32.8.68 | ||||
| 2021-12-01 | 37.48.65.149 | ||||
| 2021-12-01 | 207.244.67.215 | ||||
| 2021-12-01 | 103.224.182.207 | ||||
| 2021-12-01 | 185.107.56.59 | ||||
| 2021-12-01 | 93.115.28.104 | ||||
| 2021-12-01 | 74.63.241.23 | ||||
| 2021-11-30 | 64.32.8.68 | ||||
| 2021-11-30 | 37.48.65.149 | ||||
| 2021-11-30 | 207.244.67.215 | ||||
| 2021-11-30 | 103.224.182.207 | ||||
| 2021-11-30 | 185.107.56.59 | ||||
| 2021-11-30 | 93.115.28.104 | ||||
| 2021-11-30 | 74.63.241.23 | ||||
| 2021-11-29 | 64.32.8.68 | ||||
| 2021-11-29 | 37.48.65.149 | ||||
| 2021-11-29 | 207.244.67.215 | ||||
| 2021-11-29 | 103.224.182.207 | ||||
| 2021-11-29 | 185.107.56.59 | ||||
| 2021-11-29 | 93.115.28.104 | ||||
| 2021-11-29 | 74.63.241.23 | ||||
| 2021-11-28 | 64.32.8.68 | ||||
| 2021-11-28 | 37.48.65.149 | ||||
| 2021-11-28 | 207.244.67.215 | ||||
| 2021-11-28 | 103.224.182.207 | ||||
| 2021-11-28 | 185.107.56.59 | ||||
| 2021-11-28 | 93.115.28.104 | ||||
| 2021-11-28 | 74.63.241.23 | ||||
| 2021-11-27 | 64.32.8.68 | ||||
| 2021-11-27 | 37.48.65.149 | ||||
| 2021-11-27 | 207.244.67.215 | ||||
| 2021-11-27 | 103.224.182.207 | ||||
| 2021-11-27 | 185.107.56.59 | ||||
| 2021-11-27 | 93.115.28.104 | ||||
| 2021-11-27 | 74.63.241.23 | ||||
| 2021-11-26 | 64.32.8.68 | ||||
| 2021-11-26 | 37.48.65.149 | ||||
| 2021-11-26 | 207.244.67.215 | ||||
| 2021-11-26 | 103.224.182.207 | ||||
| 2021-11-26 | 185.107.56.59 | ||||
| 2021-11-26 | 93.115.28.104 | ||||
| 2021-11-26 | 74.63.241.23 | ||||
| 2021-11-25 | 64.32.8.68 | ||||
| 2021-11-25 | 37.48.65.149 | ||||
| 2021-11-25 | 207.244.67.215 | ||||
| 2021-11-25 | 103.224.182.207 | ||||
| 2021-11-25 | 185.107.56.59 | ||||
| 2021-11-25 | 93.115.28.104 | ||||
| 2021-11-25 | 74.63.241.23 | ||||
| 2021-11-24 | 64.32.8.68 | ||||
| 2021-11-24 | 37.48.65.149 | ||||
| 2021-11-24 | 207.244.67.215 | ||||
| 2021-11-24 | 103.224.182.207 | ||||
| 2021-11-24 | 185.107.56.59 | ||||
| 2021-11-24 | 93.115.28.104 | ||||
| 2021-11-24 | 74.63.241.23 | ||||
| 2021-11-23 | 64.32.8.68 | ||||
| 2021-11-23 | 37.48.65.149 | ||||
| 2021-11-23 | 207.244.67.215 | ||||
| 2021-11-23 | 103.224.182.207 | ||||
| 2021-11-23 | 185.107.56.59 | ||||
| 2021-11-23 | 93.115.28.104 | ||||
| 2021-11-23 | 74.63.241.23 | ||||
| 2021-11-21 | 64.32.8.68 | ||||
| 2021-11-21 | 37.48.65.149 | ||||
| 2021-11-21 | 207.244.67.215 | ||||
| 2021-11-21 | 103.224.182.207 | ||||
| 2021-11-21 | 185.107.56.59 | ||||
| 2021-11-21 | 93.115.28.104 | ||||
| 2021-11-21 | 74.63.241.23 | ||||
| 2021-11-20 | 64.32.8.68 | ||||
| 2021-11-20 | 37.48.65.149 | ||||
| 2021-11-20 | 207.244.67.215 | ||||
| 2021-11-20 | 103.224.182.207 | ||||
| 2021-11-20 | 185.107.56.59 | ||||
| 2021-11-20 | 93.115.28.104 | ||||
| 2021-11-20 | 74.63.241.23 | ||||
| 2021-11-19 | 64.32.8.68 | ||||
| 2021-11-19 | 37.48.65.149 | ||||
| 2021-11-19 | 207.244.67.215 | ||||
| 2021-11-19 | 103.224.182.207 | ||||
| 2021-11-19 | 185.107.56.59 | ||||
| 2021-11-19 | 93.115.28.104 | ||||
| 2021-11-19 | 74.63.241.23 | ||||
| 2021-11-18 | 64.32.8.68 | ||||
| 2021-11-18 | 37.48.65.149 | ||||
| 2021-11-18 | 207.244.67.215 | ||||
| 2021-11-18 | 103.224.182.207 | ||||
| 2021-11-18 | 185.107.56.59 | ||||
| 2021-11-18 | 93.115.28.104 | ||||
| 2021-11-18 | 74.63.241.23 | ||||
| 2021-11-17 | 64.32.8.68 | ||||
| 2021-11-17 | 37.48.65.149 | ||||
| 2021-11-17 | 207.244.67.215 | ||||
| 2021-11-17 | 103.224.182.207 | ||||
| 2021-11-17 | 185.107.56.59 | ||||
| 2021-11-17 | 93.115.28.104 | ||||
| 2021-11-17 | 74.63.241.23 | ||||
| 2021-11-16 | 64.32.8.68 | ||||
| 2021-11-16 | 37.48.65.149 | ||||
| 2021-11-16 | 207.244.67.215 | ||||
| 2021-11-16 | 103.224.182.207 | ||||
| 2021-11-16 | 185.107.56.59 | ||||
| 2021-11-16 | 93.115.28.104 | ||||
| 2021-11-16 | 74.63.241.23 | ||||
| 2021-11-15 | 64.32.8.68 | ||||
| 2021-11-15 | 37.48.65.149 | ||||
| 2021-11-15 | 207.244.67.215 | ||||
| 2021-11-15 | 103.224.182.207 | ||||
| 2021-11-15 | 185.107.56.59 | ||||
| 2021-11-15 | 93.115.28.104 | ||||
| 2021-11-15 | 74.63.241.23 | ||||
| 2021-11-13 | 64.32.8.68 | ||||
| 2021-11-13 | 37.48.65.149 | ||||
| 2021-11-13 | 207.244.67.215 | ||||
| 2021-11-13 | 103.224.182.207 | ||||
| 2021-11-13 | 185.107.56.59 | ||||
| 2021-11-13 | 93.115.28.104 | ||||
| 2021-11-13 | 74.63.241.23 | ||||
| 2021-11-11 | 64.32.8.68 | ||||
| 2021-11-11 | 37.48.65.149 | ||||
| 2021-11-11 | 207.244.67.215 | ||||
| 2021-11-11 | 103.224.182.207 | ||||
| 2021-11-11 | 185.107.56.59 | ||||
| 2021-11-11 | 93.115.28.104 | ||||
| 2021-11-11 | 74.63.241.23 | ||||
| 2021-11-09 | 64.32.8.68 | ||||
| 2021-11-09 | 37.48.65.149 | ||||
| 2021-11-09 | 207.244.67.215 | ||||
| 2021-11-09 | 103.224.182.207 | ||||
| 2021-11-09 | 185.107.56.59 | ||||
| 2021-11-09 | 93.115.28.104 | ||||
| 2021-11-09 | 74.63.241.23 | ||||
| 2021-11-07 | 64.32.8.68 | ||||
| 2021-11-07 | 37.48.65.149 | ||||
| 2021-11-07 | 207.244.67.215 | ||||
| 2021-11-07 | 103.224.182.207 | ||||
| 2021-11-07 | 185.107.56.59 | ||||
| 2021-11-07 | 93.115.28.104 | ||||
| 2021-11-07 | 74.63.241.23 | ||||
| 2021-11-06 | 64.32.8.68 | ||||
| 2021-11-06 | 37.48.65.149 | ||||
| 2021-11-06 | 207.244.67.215 | ||||
| 2021-11-06 | 103.224.182.207 | ||||
| 2021-11-06 | 185.107.56.59 | ||||
| 2021-11-06 | 93.115.28.104 | ||||
| 2021-11-06 | 74.63.241.23 | ||||
| 2021-11-05 | 64.32.8.68 | ||||
| 2021-11-05 | 37.48.65.149 | ||||
| 2021-11-05 | 207.244.67.215 | ||||
| 2021-11-05 | 103.224.182.207 | ||||
| 2021-11-05 | 185.107.56.59 | ||||
| 2021-11-05 | 93.115.28.104 | ||||
| 2021-11-05 | 74.63.241.23 | ||||
| 2021-11-04 | 64.32.8.68 | ||||
| 2021-11-04 | 37.48.65.149 | ||||
| 2021-11-04 | 207.244.67.215 | ||||
| 2021-11-04 | 103.224.182.207 | ||||
| 2021-11-04 | 185.107.56.59 | ||||
| 2021-11-04 | 93.115.28.104 | ||||
| 2021-11-04 | 74.63.241.23 | ||||
| 2021-11-03 | 64.32.8.68 | ||||
| 2021-11-03 | 37.48.65.149 | ||||
| 2021-11-03 | 207.244.67.215 | ||||
| 2021-11-03 | 103.224.182.207 | ||||
| 2021-11-03 | 185.107.56.59 | ||||
| 2021-11-03 | 93.115.28.104 | ||||
| 2021-11-03 | 74.63.241.23 | ||||
| 2021-11-02 | 64.32.8.68 | ||||
| 2021-11-02 | 37.48.65.149 | ||||
| 2021-11-02 | 207.244.67.215 | ||||
| 2021-11-02 | 103.224.182.207 | ||||
| 2021-11-02 | 185.107.56.59 | ||||
| 2021-11-02 | 93.115.28.104 | ||||
| 2021-11-02 | 74.63.241.23 | ||||
| 2021-11-01 | 64.32.8.68 | ||||
| 2021-11-01 | 37.48.65.149 | ||||
| 2021-11-01 | 207.244.67.215 | ||||
| 2021-11-01 | 103.224.182.207 | ||||
| 2021-11-01 | 185.107.56.59 | ||||
| 2021-11-01 | 93.115.28.104 | ||||
| 2021-11-01 | 74.63.241.23 | ||||
| 2021-10-31 | 64.32.8.68 | ||||
| 2021-10-31 | 37.48.65.149 | ||||
| 2021-10-31 | 207.244.67.215 | ||||
| 2021-10-31 | 103.224.182.207 | ||||
| 2021-10-31 | 185.107.56.59 | ||||
| 2021-10-31 | 93.115.28.104 | ||||
| 2021-10-31 | 74.63.241.23 | ||||
| 2021-10-30 | 64.32.8.68 | ||||
| 2021-10-30 | 37.48.65.149 | ||||
| 2021-10-30 | 207.244.67.215 | ||||
| 2021-10-30 | 103.224.182.207 | ||||
| 2021-10-30 | 185.107.56.59 | ||||
| 2021-10-30 | 93.115.28.104 | ||||
| 2021-10-30 | 74.63.241.23 | ||||
| 2021-10-29 | 64.32.8.68 | ||||
| 2021-10-29 | 37.48.65.149 | ||||
| 2021-10-29 | 207.244.67.215 | ||||
| 2021-10-29 | 103.224.182.207 | ||||
| 2021-10-29 | 185.107.56.59 | ||||
| 2021-10-29 | 93.115.28.104 | ||||
| 2021-10-29 | 74.63.241.23 | ||||
| 2021-10-28 | 64.32.8.68 | ||||
| 2021-10-28 | 37.48.65.149 | ||||
| 2021-10-28 | 207.244.67.215 | ||||
| 2021-10-28 | 103.224.182.207 | ||||
| 2021-10-28 | 185.107.56.59 | ||||
| 2021-10-28 | 93.115.28.104 | ||||
| 2021-10-28 | 74.63.241.23 | ||||
| 2021-10-27 | 64.32.8.68 | ||||
| 2021-10-27 | 37.48.65.149 | ||||
| 2021-10-27 | 207.244.67.215 | ||||
| 2021-10-27 | 103.224.182.207 | ||||
| 2021-10-27 | 185.107.56.59 | ||||
| 2021-10-27 | 93.115.28.104 | ||||
| 2021-10-27 | 74.63.241.23 | ||||
| 2021-10-25 | 64.32.8.68 | ||||
| 2021-10-25 | 37.48.65.149 | ||||
| 2021-10-25 | 207.244.67.215 | ||||
| 2021-10-25 | 103.224.182.207 | ||||
| 2021-10-25 | 185.107.56.59 | ||||
| 2021-10-25 | 93.115.28.104 | ||||
| 2021-10-25 | 74.63.241.23 | ||||
| 2021-10-24 | 64.32.8.68 | ||||
| 2021-10-24 | 37.48.65.149 | ||||
| 2021-10-24 | 207.244.67.215 | ||||
| 2021-10-24 | 103.224.182.207 | ||||
| 2021-10-24 | 185.107.56.59 | ||||
| 2021-10-24 | 93.115.28.104 | ||||
| 2021-10-24 | 74.63.241.23 | ||||
| 2021-10-23 | 64.32.8.68 | ||||
| 2021-10-23 | 37.48.65.149 | ||||
| 2021-10-23 | 207.244.67.215 | ||||
| 2021-10-23 | 103.224.182.207 | ||||
| 2021-10-23 | 185.107.56.59 | ||||
| 2021-10-23 | 93.115.28.104 | ||||
| 2021-10-23 | 74.63.241.23 | ||||
| 2021-10-22 | 64.32.8.68 | ||||
| 2021-10-22 | 37.48.65.149 | ||||
| 2021-10-22 | 207.244.67.215 | ||||
| 2021-10-22 | 103.224.182.207 | ||||
| 2021-10-22 | 185.107.56.59 | ||||
| 2021-10-22 | 93.115.28.104 | ||||
| 2021-10-22 | 74.63.241.23 | ||||
| 2021-10-21 | 64.32.8.68 | ||||
| 2021-10-21 | 37.48.65.149 | ||||
| 2021-10-21 | 207.244.67.215 | ||||
| 2021-10-21 | 103.224.182.207 | ||||
| 2021-10-21 | 185.107.56.59 | ||||
| 2021-10-21 | 93.115.28.104 | ||||
| 2021-10-21 | 74.63.241.23 | ||||
| 2021-10-20 | 64.32.8.68 | ||||
| 2021-10-20 | 37.48.65.149 | ||||
| 2021-10-20 | 207.244.67.215 | ||||
| 2021-10-20 | 103.224.182.207 | ||||
| 2021-10-20 | 185.107.56.59 | ||||
| 2021-10-20 | 93.115.28.104 | ||||
| 2021-10-20 | 74.63.241.23 | ||||
| 2021-10-19 | 64.32.8.68 | ||||
| 2021-10-19 | 37.48.65.149 | ||||
| 2021-10-19 | 207.244.67.215 | ||||
| 2021-10-19 | 103.224.182.207 | ||||
| 2021-10-19 | 185.107.56.59 | ||||
| 2021-10-19 | 93.115.28.104 | ||||
| 2021-10-19 | 74.63.241.23 | ||||
| 2021-10-18 | 64.32.8.68 | ||||
| 2021-10-18 | 37.48.65.149 | ||||
| 2021-10-18 | 207.244.67.215 | ||||
| 2021-10-18 | 103.224.182.207 | ||||
| 2021-10-18 | 185.107.56.59 | ||||
| 2021-10-18 | 93.115.28.104 | ||||
| 2021-10-18 | 74.63.241.23 | ||||
| 2021-10-17 | 64.32.8.68 | ||||
| 2021-10-17 | 37.48.65.149 | ||||
| 2021-10-17 | 207.244.67.215 | ||||
| 2021-10-17 | 103.224.182.207 | ||||
| 2021-10-17 | 185.107.56.59 | ||||
| 2021-10-17 | 93.115.28.104 | ||||
| 2021-10-17 | 74.63.241.23 | ||||
| 2021-10-16 | 64.32.8.68 | ||||
| 2021-10-16 | 37.48.65.149 | ||||
| 2021-10-16 | 207.244.67.215 | ||||
| 2021-10-16 | 103.224.182.207 | ||||
| 2021-10-16 | 185.107.56.59 | ||||
| 2021-10-16 | 93.115.28.104 | ||||
| 2021-10-16 | 74.63.241.23 | ||||
| 2021-10-15 | 64.32.8.68 | ||||
| 2021-10-15 | 37.48.65.149 | ||||
| 2021-10-15 | 207.244.67.215 | ||||
| 2021-10-15 | 103.224.182.207 | ||||
| 2021-10-15 | 185.107.56.59 | ||||
| 2021-10-15 | 93.115.28.104 | ||||
| 2021-10-15 | 74.63.241.23 | ||||
| 2021-10-14 | 64.32.8.68 | ||||
| 2021-10-14 | 37.48.65.149 | ||||
| 2021-10-14 | 207.244.67.215 | ||||
| 2021-10-14 | 103.224.182.207 | ||||
| 2021-10-14 | 185.107.56.59 | ||||
| 2021-10-14 | 93.115.28.104 | ||||
| 2021-10-14 | 74.63.241.23 | ||||
| 2021-10-13 | 64.32.8.68 | ||||
| 2021-10-13 | 37.48.65.149 | ||||
| 2021-10-13 | 207.244.67.215 | ||||
| 2021-10-13 | 103.224.182.207 | ||||
| 2021-10-13 | 185.107.56.59 | ||||
| 2021-10-13 | 93.115.28.104 | ||||
| 2021-10-13 | 74.63.241.23 | ||||
| 2021-10-12 | 64.32.8.68 | ||||
| 2021-10-12 | 37.48.65.149 | ||||
| 2021-10-12 | 207.244.67.215 | ||||
| 2021-10-12 | 103.224.182.207 | ||||
| 2021-10-12 | 185.107.56.59 | ||||
| 2021-10-12 | 93.115.28.104 | ||||
| 2021-10-12 | 74.63.241.23 | ||||
| 2021-10-11 | 64.32.8.68 | ||||
| 2021-10-11 | 37.48.65.149 | ||||
| 2021-10-11 | 207.244.67.215 | ||||
| 2021-10-11 | 103.224.182.207 | ||||
| 2021-10-11 | 185.107.56.59 | ||||
| 2021-10-11 | 93.115.28.104 | ||||
| 2021-10-11 | 74.63.241.23 | ||||
| 2021-10-10 | 64.32.8.68 | ||||
| 2021-10-10 | 37.48.65.149 | ||||
| 2021-10-10 | 207.244.67.215 | ||||
| 2021-10-10 | 103.224.182.207 | ||||
| 2021-10-10 | 185.107.56.59 | ||||
| 2021-10-10 | 93.115.28.104 | ||||
| 2021-10-10 | 74.63.241.23 | ||||
| 2021-10-09 | 64.32.8.68 | ||||
| 2021-10-09 | 37.48.65.149 | ||||
| 2021-10-09 | 207.244.67.215 | ||||
| 2021-10-09 | 103.224.182.207 | ||||
| 2021-10-09 | 185.107.56.59 | ||||
| 2021-10-09 | 93.115.28.104 | ||||
| 2021-10-09 | 74.63.241.23 | ||||
| 2021-10-08 | 64.32.8.68 | ||||
| 2021-10-08 | 37.48.65.149 | ||||
| 2021-10-08 | 207.244.67.215 | ||||
| 2021-10-08 | 103.224.182.207 | ||||
| 2021-10-08 | 185.107.56.59 | ||||
| 2021-10-08 | 93.115.28.104 | ||||
| 2021-10-08 | 74.63.241.23 | ||||
| 2021-10-07 | 64.32.8.68 | ||||
| 2021-10-07 | 37.48.65.149 | ||||
| 2021-10-07 | 207.244.67.215 | ||||
| 2021-10-07 | 103.224.182.207 | ||||
| 2021-10-07 | 185.107.56.59 | ||||
| 2021-10-07 | 93.115.28.104 | ||||
| 2021-10-07 | 74.63.241.23 | ||||
| 2021-10-06 | 64.32.8.68 | ||||
| 2021-10-06 | 37.48.65.149 | ||||
| 2021-10-06 | 207.244.67.215 | ||||
| 2021-10-06 | 103.224.182.207 | ||||
| 2021-10-06 | 185.107.56.59 | ||||
| 2021-10-06 | 93.115.28.104 | ||||
| 2021-10-06 | 74.63.241.23 | ||||
| 2021-10-05 | 64.32.8.68 | ||||
| 2021-10-05 | 37.48.65.149 | ||||
| 2021-10-05 | 207.244.67.215 | ||||
| 2021-10-05 | 103.224.182.207 | ||||
| 2021-10-05 | 185.107.56.59 | ||||
| 2021-10-05 | 93.115.28.104 | ||||
| 2021-10-05 | 74.63.241.23 | ||||
| 2021-10-04 | 64.32.8.68 | ||||
| 2021-10-04 | 37.48.65.149 | ||||
| 2021-10-04 | 207.244.67.215 | ||||
| 2021-10-04 | 103.224.182.207 | ||||
| 2021-10-04 | 185.107.56.59 | ||||
| 2021-10-04 | 93.115.28.104 | ||||
| 2021-10-04 | 74.63.241.23 | ||||
| 2021-10-03 | 64.32.8.68 | ||||
| 2021-10-03 | 37.48.65.149 | ||||
| 2021-10-03 | 207.244.67.215 | ||||
| 2021-10-03 | 103.224.182.207 | ||||
| 2021-10-03 | 185.107.56.59 | ||||
| 2021-10-03 | 93.115.28.104 | ||||
| 2021-10-03 | 74.63.241.23 | ||||
| 2021-10-02 | 64.32.8.68 | ||||
| 2021-10-02 | 37.48.65.149 | ||||
| 2021-10-02 | 207.244.67.215 | ||||
| 2021-10-02 | 103.224.182.207 | ||||
| 2021-10-02 | 185.107.56.59 | ||||
| 2021-10-02 | 93.115.28.104 | ||||
| 2021-10-02 | 74.63.241.23 | ||||
| 2021-10-01 | 64.32.8.68 | ||||
| 2021-10-01 | 37.48.65.149 | ||||
| 2021-10-01 | 207.244.67.215 | ||||
| 2021-10-01 | 103.224.182.207 | ||||
| 2021-10-01 | 185.107.56.59 | ||||
| 2021-10-01 | 93.115.28.104 | ||||
| 2021-10-01 | 74.63.241.23 | ||||
| 2021-09-30 | 64.32.8.68 | ||||
| 2021-09-30 | 37.48.65.149 | ||||
| 2021-09-30 | 207.244.67.215 | ||||
| 2021-09-30 | 103.224.182.207 | ||||
| 2021-09-30 | 185.107.56.59 | ||||
| 2021-09-30 | 93.115.28.104 | ||||
| 2021-09-30 | 74.63.241.23 | ||||
| 2021-09-29 | 64.32.8.68 | ||||
| 2021-09-29 | 37.48.65.149 | ||||
| 2021-09-29 | 207.244.67.215 | ||||
| 2021-09-29 | 103.224.182.207 | ||||
| 2021-09-29 | 185.107.56.59 | ||||
| 2021-09-29 | 93.115.28.104 | ||||
| 2021-09-29 | 74.63.241.23 | ||||
| 2021-09-23 | 64.32.8.68 | ||||
| 2021-09-23 | 37.48.65.149 | ||||
| 2021-09-23 | 207.244.67.215 | ||||
| 2021-09-23 | 103.224.182.207 | ||||
| 2021-09-23 | 185.107.56.59 | ||||
| 2021-09-23 | 93.115.28.104 | ||||
| 2021-09-23 | 74.63.241.23 | ||||
| 2021-09-22 | 64.32.8.68 | ||||
| 2021-09-22 | 37.48.65.149 | ||||
| 2021-09-22 | 207.244.67.215 | ||||
| 2021-09-22 | 103.224.182.207 | ||||
| 2021-09-22 | 185.107.56.59 | ||||
| 2021-09-22 | 93.115.28.104 | ||||
| 2021-09-22 | 74.63.241.23 | ||||
| 2021-09-21 | 64.32.8.68 | ||||
| 2021-09-21 | 37.48.65.149 | ||||
| 2021-09-21 | 207.244.67.215 | ||||
| 2021-09-21 | 103.224.182.207 | ||||
| 2021-09-21 | 185.107.56.59 | ||||
| 2021-09-21 | 93.115.28.104 | ||||
| 2021-09-21 | 74.63.241.23 | ||||
| 2021-09-20 | 64.32.8.68 | ||||
| 2021-09-20 | 37.48.65.149 | ||||
| 2021-09-20 | 207.244.67.215 | ||||
| 2021-09-20 | 103.224.182.207 | ||||
| 2021-09-20 | 185.107.56.59 | ||||
| 2021-09-20 | 93.115.28.104 | ||||
| 2021-09-20 | 74.63.241.23 | ||||
| 2021-09-19 | 64.32.8.68 | ||||
| 2021-09-19 | 37.48.65.149 | ||||
| 2021-09-19 | 207.244.67.215 | ||||
| 2021-09-19 | 103.224.182.207 | ||||
| 2021-09-19 | 185.107.56.59 | ||||
| 2021-09-19 | 93.115.28.104 | ||||
| 2021-09-19 | 74.63.241.23 | ||||
| 2021-09-18 | 64.32.8.68 | ||||
| 2021-09-18 | 37.48.65.149 | ||||
| 2021-09-18 | 207.244.67.215 | ||||
| 2021-09-18 | 103.224.182.207 | ||||
| 2021-09-18 | 185.107.56.59 | ||||
| 2021-09-18 | 93.115.28.104 | ||||
| 2021-09-18 | 74.63.241.23 | ||||
| 2021-09-17 | 64.32.8.68 | ||||
| 2021-09-17 | 37.48.65.149 | ||||
| 2021-09-17 | 207.244.67.215 | ||||
| 2021-09-17 | 103.224.182.207 | ||||
| 2021-09-17 | 185.107.56.59 | ||||
| 2021-09-17 | 93.115.28.104 | ||||
| 2021-09-17 | 74.63.241.23 | ||||
| 2021-09-16 | 64.32.8.68 | ||||
| 2021-09-16 | 37.48.65.149 | ||||
| 2021-09-16 | 207.244.67.215 | ||||
| 2021-09-16 | 103.224.182.207 | ||||
| 2021-09-16 | 185.107.56.59 | ||||
| 2021-09-16 | 93.115.28.104 | ||||
| 2021-09-16 | 74.63.241.23 | ||||
| 2021-09-15 | 64.32.8.68 | ||||
| 2021-09-15 | 37.48.65.149 | ||||
| 2021-09-15 | 207.244.67.215 | ||||
| 2021-09-15 | 103.224.182.207 | ||||
| 2021-09-15 | 185.107.56.59 | ||||
| 2021-09-15 | 93.115.28.104 | ||||
| 2021-09-15 | 74.63.241.23 | ||||
| 2021-09-14 | 64.32.8.68 | ||||
| 2021-09-14 | 37.48.65.149 | ||||
| 2021-09-14 | 207.244.67.215 | ||||
| 2021-09-14 | 103.224.182.207 | ||||
| 2021-09-14 | 185.107.56.59 | ||||
| 2021-09-14 | 93.115.28.104 | ||||
| 2021-09-14 | 74.63.241.23 | ||||
| 2021-09-13 | 64.32.8.68 | ||||
| 2021-09-13 | 37.48.65.149 | ||||
| 2021-09-13 | 207.244.67.215 | ||||
| 2021-09-13 | 103.224.182.207 | ||||
| 2021-09-13 | 185.107.56.59 | ||||
| 2021-09-13 | 93.115.28.104 | ||||
| 2021-09-13 | 74.63.241.23 | ||||
| 2021-09-12 | 64.32.8.68 | ||||
| 2021-09-12 | 37.48.65.149 | ||||
| 2021-09-12 | 207.244.67.215 | ||||
| 2021-09-12 | 103.224.182.207 | ||||
| 2021-09-12 | 185.107.56.59 | ||||
| 2021-09-12 | 93.115.28.104 | ||||
| 2021-09-12 | 74.63.241.23 | ||||
| 2021-09-11 | 64.32.8.68 | ||||
| 2021-09-11 | 37.48.65.149 | ||||
| 2021-09-11 | 207.244.67.215 | ||||
| 2021-09-11 | 103.224.182.207 | ||||
| 2021-09-11 | 185.107.56.59 | ||||
| 2021-09-11 | 93.115.28.104 | ||||
| 2021-09-11 | 74.63.241.23 | ||||
| 2021-09-10 | 64.32.8.68 | ||||
| 2021-09-10 | 37.48.65.149 | ||||
| 2021-09-10 | 207.244.67.215 | ||||
| 2021-09-10 | 103.224.182.207 | ||||
| 2021-09-10 | 185.107.56.59 | ||||
| 2021-09-10 | 93.115.28.104 | ||||
| 2021-09-10 | 74.63.241.23 | ||||
| 2021-09-09 | 64.32.8.68 | ||||
| 2021-09-09 | 37.48.65.149 | ||||
| 2021-09-09 | 207.244.67.215 | ||||
| 2021-09-09 | 103.224.182.207 | ||||
| 2021-09-09 | 185.107.56.59 | ||||
| 2021-09-09 | 93.115.28.104 | ||||
| 2021-09-09 | 74.63.241.23 | ||||
| 2021-09-08 | 64.32.8.68 | ||||
| 2021-09-08 | 37.48.65.149 | ||||
| 2021-09-08 | 207.244.67.215 | ||||
| 2021-09-08 | 103.224.182.207 | ||||
| 2021-09-08 | 185.107.56.59 | ||||
| 2021-09-08 | 93.115.28.104 | ||||
| 2021-09-08 | 74.63.241.23 | ||||
| 2021-09-07 | 64.32.8.68 | ||||
| 2021-09-07 | 37.48.65.149 | ||||
| 2021-09-07 | 207.244.67.215 | ||||
| 2021-09-07 | 103.224.182.207 | ||||
| 2021-09-07 | 185.107.56.59 | ||||
| 2021-09-07 | 93.115.28.104 | ||||
| 2021-09-07 | 74.63.241.23 | ||||
| 2021-09-06 | 64.32.8.68 | ||||
| 2021-09-06 | 37.48.65.149 | ||||
| 2021-09-06 | 207.244.67.215 | ||||
| 2021-09-06 | 103.224.182.207 | ||||
| 2021-09-06 | 185.107.56.59 | ||||
| 2021-09-06 | 93.115.28.104 | ||||
| 2021-09-06 | 74.63.241.23 | ||||
| 2021-09-05 | 64.32.8.68 | ||||
| 2021-09-05 | 37.48.65.149 | ||||
| 2021-09-05 | 207.244.67.215 | ||||
| 2021-09-05 | 103.224.182.207 | ||||
| 2021-09-05 | 185.107.56.59 | ||||
| 2021-09-05 | 93.115.28.104 | ||||
| 2021-09-05 | 74.63.241.23 | ||||
| 2021-09-04 | 64.32.8.68 | ||||
| 2021-09-04 | 37.48.65.149 | ||||
| 2021-09-04 | 207.244.67.215 | ||||
| 2021-09-04 | 103.224.182.207 | ||||
| 2021-09-04 | 185.107.56.59 | ||||
| 2021-09-04 | 93.115.28.104 | ||||
| 2021-09-04 | 74.63.241.23 | ||||
| 2021-09-03 | 64.32.8.68 | ||||
| 2021-09-03 | 37.48.65.149 | ||||
| 2021-09-03 | 207.244.67.215 | ||||
| 2021-09-03 | 103.224.182.207 | ||||
| 2021-09-03 | 185.107.56.59 | ||||
| 2021-09-03 | 93.115.28.104 | ||||
| 2021-09-03 | 74.63.241.23 | ||||
| 2021-09-02 | 64.32.8.68 | ||||
| 2021-09-02 | 37.48.65.149 | ||||
| 2021-09-02 | 207.244.67.215 | ||||
| 2021-09-02 | 103.224.182.207 | ||||
| 2021-09-02 | 185.107.56.59 | ||||
| 2021-09-02 | 93.115.28.104 | ||||
| 2021-09-02 | 74.63.241.23 | ||||
| 2021-09-01 | 64.32.8.68 | ||||
| 2021-09-01 | 37.48.65.149 | ||||
| 2021-09-01 | 207.244.67.215 | ||||
| 2021-09-01 | 103.224.182.207 | ||||
| 2021-09-01 | 185.107.56.59 | ||||
| 2021-09-01 | 93.115.28.104 | ||||
| 2021-09-01 | 74.63.241.23 | ||||
| 2021-08-31 | 64.32.8.68 | ||||
| 2021-08-31 | 37.48.65.149 | ||||
| 2021-08-31 | 207.244.67.215 | ||||
| 2021-08-31 | 103.224.182.207 | ||||
| 2021-08-31 | 185.107.56.59 | ||||
| 2021-08-31 | 93.115.28.104 | ||||
| 2021-08-31 | 74.63.241.23 | ||||
| 2021-08-30 | 64.32.8.68 | ||||
| 2021-08-30 | 37.48.65.149 | ||||
| 2021-08-30 | 207.244.67.215 | ||||
| 2021-08-30 | 103.224.182.207 | ||||
| 2021-08-30 | 185.107.56.59 | ||||
| 2021-08-30 | 93.115.28.104 | ||||
| 2021-08-30 | 74.63.241.23 | ||||
| 2021-08-29 | 64.32.8.68 | ||||
| 2021-08-29 | 37.48.65.149 | ||||
| 2021-08-29 | 207.244.67.215 | ||||
| 2021-08-29 | 103.224.182.207 | ||||
| 2021-08-29 | 185.107.56.59 | ||||
| 2021-08-29 | 93.115.28.104 | ||||
| 2021-08-29 | 74.63.241.23 | ||||
| 2021-08-28 | 64.32.8.68 | ||||
| 2021-08-28 | 37.48.65.149 | ||||
| 2021-08-28 | 207.244.67.215 | ||||
| 2021-08-28 | 103.224.182.207 | ||||
| 2021-08-28 | 185.107.56.59 | ||||
| 2021-08-28 | 93.115.28.104 | ||||
| 2021-08-28 | 74.63.241.23 | ||||
| 2021-08-27 | 64.32.8.68 | ||||
| 2021-08-27 | 37.48.65.149 | ||||
| 2021-08-27 | 207.244.67.215 | ||||
| 2021-08-27 | 103.224.182.207 | ||||
| 2021-08-27 | 185.107.56.59 | ||||
| 2021-08-27 | 93.115.28.104 | ||||
| 2021-08-27 | 74.63.241.23 | ||||
| 2021-08-26 | 64.32.8.68 | ||||
| 2021-08-26 | 37.48.65.149 | ||||
| 2021-08-26 | 207.244.67.215 | ||||
| 2021-08-26 | 103.224.182.207 | ||||
| 2021-08-26 | 185.107.56.59 | ||||
| 2021-08-26 | 93.115.28.104 | ||||
| 2021-08-26 | 74.63.241.23 | ||||
| 2021-08-25 | 64.32.8.68 | ||||
| 2021-08-25 | 37.48.65.149 | ||||
| 2021-08-25 | 207.244.67.215 | ||||
| 2021-08-25 | 103.224.182.207 | ||||
| 2021-08-25 | 185.107.56.59 | ||||
| 2021-08-25 | 93.115.28.104 | ||||
| 2021-08-25 | 74.63.241.23 | ||||
| 2021-08-24 | 64.32.8.68 | ||||
| 2021-08-24 | 37.48.65.149 | ||||
| 2021-08-24 | 207.244.67.215 | ||||
| 2021-08-24 | 103.224.182.207 | ||||
| 2021-08-24 | 185.107.56.59 | ||||
| 2021-08-24 | 93.115.28.104 | ||||
| 2021-08-24 | 74.63.241.23 | ||||
| 2021-08-23 | 64.32.8.68 | ||||
| 2021-08-23 | 37.48.65.149 | ||||
| 2021-08-23 | 207.244.67.215 | ||||
| 2021-08-23 | 103.224.182.207 | ||||
| 2021-08-23 | 185.107.56.59 | ||||
| 2021-08-23 | 93.115.28.104 | ||||
| 2021-08-23 | 74.63.241.23 | ||||
| 2021-08-22 | 64.32.8.68 | ||||
| 2021-08-22 | 37.48.65.149 | ||||
| 2021-08-22 | 207.244.67.215 | ||||
| 2021-08-22 | 103.224.182.207 | ||||
| 2021-08-22 | 185.107.56.59 | ||||
| 2021-08-22 | 93.115.28.104 | ||||
| 2021-08-22 | 74.63.241.23 | ||||
| 2021-08-21 | 64.32.8.68 | ||||
| 2021-08-21 | 37.48.65.149 | ||||
| 2021-08-21 | 207.244.67.215 | ||||
| 2021-08-21 | 103.224.182.207 | ||||
| 2021-08-21 | 185.107.56.59 | ||||
| 2021-08-21 | 93.115.28.104 | ||||
| 2021-08-21 | 74.63.241.23 | ||||
| 2021-08-20 | 64.32.8.68 | ||||
| 2021-08-20 | 37.48.65.149 | ||||
| 2021-08-20 | 207.244.67.215 | ||||
| 2021-08-20 | 103.224.182.207 | ||||
| 2021-08-20 | 185.107.56.59 | ||||
| 2021-08-20 | 93.115.28.104 | ||||
| 2021-08-20 | 74.63.241.23 | ||||
| 2021-08-19 | 64.32.8.68 | ||||
| 2021-08-19 | 37.48.65.149 | ||||
| 2021-08-19 | 207.244.67.215 | ||||
| 2021-08-19 | 103.224.182.207 | ||||
| 2021-08-19 | 185.107.56.59 | ||||
| 2021-08-19 | 93.115.28.104 | ||||
| 2021-08-19 | 74.63.241.23 | ||||
| 2021-08-18 | 64.32.8.68 | ||||
| 2021-08-18 | 37.48.65.149 | ||||
| 2021-08-18 | 207.244.67.215 | ||||
| 2021-08-18 | 103.224.182.207 | ||||
| 2021-08-18 | 185.107.56.59 | ||||
| 2021-08-18 | 93.115.28.104 | ||||
| 2021-08-18 | 74.63.241.23 | ||||
| 2021-08-17 | 64.32.8.68 | ||||
| 2021-08-17 | 37.48.65.149 | ||||
| 2021-08-17 | 207.244.67.215 | ||||
| 2021-08-17 | 103.224.182.207 | ||||
| 2021-08-17 | 185.107.56.59 | ||||
| 2021-08-17 | 93.115.28.104 | ||||
| 2021-08-17 | 74.63.241.23 | ||||
| 2021-08-16 | 64.32.8.68 | ||||
| 2021-08-16 | 37.48.65.149 | ||||
| 2021-08-16 | 207.244.67.215 | ||||
| 2021-08-16 | 103.224.182.207 | ||||
| 2021-08-16 | 185.107.56.59 | ||||
| 2021-08-16 | 93.115.28.104 | ||||
| 2021-08-16 | 74.63.241.23 | ||||
| 2021-08-15 | 64.32.8.68 | ||||
| 2021-08-15 | 37.48.65.149 | ||||
| 2021-08-15 | 207.244.67.215 | ||||
| 2021-08-15 | 103.224.182.207 | ||||
| 2021-08-15 | 185.107.56.59 | ||||
| 2021-08-15 | 93.115.28.104 | ||||
| 2021-08-15 | 74.63.241.23 | ||||
| 2021-08-14 | 64.32.8.68 | ||||
| 2021-08-14 | 37.48.65.149 | ||||
| 2021-08-14 | 207.244.67.215 | ||||
| 2021-08-14 | 103.224.182.207 | ||||
| 2021-08-14 | 185.107.56.59 | ||||
| 2021-08-14 | 93.115.28.104 | ||||
| 2021-08-14 | 74.63.241.23 | ||||
| 2021-08-13 | 64.32.8.68 | ||||
| 2021-08-13 | 37.48.65.149 | ||||
| 2021-08-13 | 207.244.67.215 | ||||
| 2021-08-13 | 103.224.182.207 | ||||
| 2021-08-13 | 185.107.56.59 | ||||
| 2021-08-13 | 93.115.28.104 | ||||
| 2021-08-13 | 74.63.241.23 | ||||
| 2021-08-12 | 64.32.8.68 | ||||
| 2021-08-12 | 37.48.65.149 | ||||
| 2021-08-12 | 207.244.67.215 | ||||
| 2021-08-12 | 103.224.182.207 | ||||
| 2021-08-12 | 185.107.56.59 | ||||
| 2021-08-12 | 93.115.28.104 | ||||
| 2021-08-12 | 74.63.241.23 | ||||
| 2021-08-11 | 64.32.8.68 | ||||
| 2021-08-11 | 37.48.65.149 | ||||
| 2021-08-11 | 207.244.67.215 | ||||
| 2021-08-11 | 103.224.182.207 | ||||
| 2021-08-11 | 185.107.56.59 | ||||
| 2021-08-11 | 93.115.28.104 | ||||
| 2021-08-11 | 74.63.241.23 | ||||
| 2021-08-10 | 64.32.8.68 | ||||
| 2021-08-10 | 37.48.65.149 | ||||
| 2021-08-10 | 207.244.67.215 | ||||
| 2021-08-10 | 103.224.182.207 | ||||
| 2021-08-10 | 185.107.56.59 | ||||
| 2021-08-10 | 93.115.28.104 | ||||
| 2021-08-10 | 74.63.241.23 | ||||
| 2021-08-09 | 64.32.8.68 | ||||
| 2021-08-09 | 37.48.65.149 | ||||
| 2021-08-09 | 207.244.67.215 | ||||
| 2021-08-09 | 103.224.182.207 | ||||
| 2021-08-09 | 185.107.56.59 | ||||
| 2021-08-09 | 93.115.28.104 | ||||
| 2021-08-09 | 74.63.241.23 | ||||
| 2021-08-08 | 64.32.8.68 | ||||
| 2021-08-08 | 37.48.65.149 | ||||
| 2021-08-08 | 207.244.67.215 | ||||
| 2021-08-08 | 103.224.182.207 | ||||
| 2021-08-08 | 185.107.56.59 | ||||
| 2021-08-08 | 93.115.28.104 | ||||
| 2021-08-08 | 74.63.241.23 | ||||
| 2021-08-07 | 64.32.8.68 | ||||
| 2021-08-07 | 37.48.65.149 | ||||
| 2021-08-07 | 207.244.67.215 | ||||
| 2021-08-07 | 103.224.182.207 | ||||
| 2021-08-07 | 185.107.56.59 | ||||
| 2021-08-07 | 93.115.28.104 | ||||
| 2021-08-07 | 74.63.241.23 | ||||
| 2021-08-06 | 64.32.8.68 | ||||
| 2021-08-06 | 37.48.65.149 | ||||
| 2021-08-06 | 207.244.67.215 | ||||
| 2021-08-06 | 103.224.182.207 | ||||
| 2021-08-06 | 185.107.56.59 | ||||
| 2021-08-06 | 93.115.28.104 | ||||
| 2021-08-06 | 74.63.241.23 | ||||
| 2021-08-05 | 64.32.8.68 | ||||
| 2021-08-05 | 37.48.65.149 | ||||
| 2021-08-05 | 207.244.67.215 | ||||
| 2021-08-05 | 103.224.182.207 | ||||
| 2021-08-05 | 185.107.56.59 | ||||
| 2021-08-05 | 93.115.28.104 | ||||
| 2021-08-05 | 74.63.241.23 | ||||
| 2021-08-04 | 64.32.8.68 | ||||
| 2021-08-04 | 37.48.65.149 | ||||
| 2021-08-04 | 207.244.67.215 | ||||
| 2021-08-04 | 103.224.182.207 | ||||
| 2021-08-04 | 185.107.56.59 | ||||
| 2021-08-04 | 93.115.28.104 | ||||
| 2021-08-04 | 74.63.241.23 | ||||
| 2021-08-03 | 64.32.8.68 | ||||
| 2021-08-03 | 37.48.65.149 | ||||
| 2021-08-03 | 207.244.67.215 | ||||
| 2021-08-03 | 103.224.182.207 | ||||
| 2021-08-03 | 185.107.56.59 | ||||
| 2021-08-03 | 93.115.28.104 | ||||
| 2021-08-03 | 74.63.241.23 | ||||
| 2021-08-02 | 64.32.8.68 | ||||
| 2021-08-02 | 37.48.65.149 | ||||
| 2021-08-02 | 207.244.67.215 | ||||
| 2021-08-02 | 103.224.182.207 | ||||
| 2021-08-02 | 185.107.56.59 | ||||
| 2021-08-02 | 93.115.28.104 | ||||
| 2021-08-02 | 74.63.241.23 | ||||
| 2021-08-01 | 64.32.8.68 | ||||
| 2021-08-01 | 37.48.65.149 | ||||
| 2021-08-01 | 207.244.67.215 | ||||
| 2021-08-01 | 103.224.182.207 | ||||
| 2021-08-01 | 185.107.56.59 | ||||
| 2021-08-01 | 93.115.28.104 | ||||
| 2021-08-01 | 74.63.241.23 | ||||
| 2021-07-31 | 64.32.8.68 | ||||
| 2021-07-31 | 37.48.65.149 | ||||
| 2021-07-31 | 207.244.67.215 | ||||
| 2021-07-31 | 103.224.182.207 | ||||
| 2021-07-31 | 185.107.56.59 | ||||
| 2021-07-31 | 93.115.28.104 | ||||
| 2021-07-31 | 74.63.241.23 | ||||
| 2021-07-30 | 64.32.8.68 | ||||
| 2021-07-30 | 37.48.65.149 | ||||
| 2021-07-30 | 207.244.67.215 | ||||
| 2021-07-30 | 103.224.182.207 | ||||
| 2021-07-30 | 185.107.56.59 | ||||
| 2021-07-30 | 93.115.28.104 | ||||
| 2021-07-30 | 74.63.241.23 | ||||
| 2021-07-29 | 64.32.8.68 | ||||
| 2021-07-29 | 37.48.65.149 | ||||
| 2021-07-29 | 207.244.67.215 | ||||
| 2021-07-29 | 103.224.182.207 | ||||
| 2021-07-29 | 185.107.56.59 | ||||
| 2021-07-29 | 93.115.28.104 | ||||
| 2021-07-29 | 74.63.241.23 | ||||
| 2021-07-28 | 64.32.8.68 | ||||
| 2021-07-28 | 37.48.65.149 | ||||
| 2021-07-28 | 207.244.67.215 | ||||
| 2021-07-28 | 103.224.182.207 | ||||
| 2021-07-28 | 185.107.56.59 | ||||
| 2021-07-28 | 93.115.28.104 | ||||
| 2021-07-28 | 74.63.241.23 | ||||
| 2021-07-27 | 64.32.8.68 | ||||
| 2021-07-27 | 37.48.65.149 | ||||
| 2021-07-27 | 207.244.67.215 | ||||
| 2021-07-27 | 103.224.182.207 | ||||
| 2021-07-27 | 185.107.56.59 | ||||
| 2021-07-27 | 93.115.28.104 | ||||
| 2021-07-27 | 74.63.241.23 | ||||
| 2021-07-26 | 64.32.8.68 | ||||
| 2021-07-26 | 37.48.65.149 | ||||
| 2021-07-26 | 207.244.67.215 | ||||
| 2021-07-26 | 103.224.182.207 | ||||
| 2021-07-26 | 185.107.56.59 | ||||
| 2021-07-26 | 93.115.28.104 | ||||
| 2021-07-26 | 74.63.241.23 | ||||
| 2021-07-25 | 64.32.8.68 | ||||
| 2021-07-25 | 37.48.65.149 | ||||
| 2021-07-25 | 207.244.67.215 | ||||
| 2021-07-25 | 103.224.182.207 | ||||
| 2021-07-25 | 185.107.56.59 | ||||
| 2021-07-25 | 93.115.28.104 | ||||
| 2021-07-25 | 74.63.241.23 | ||||
| 2021-07-24 | 64.32.8.68 | ||||
| 2021-07-24 | 37.48.65.149 | ||||
| 2021-07-24 | 207.244.67.215 | ||||
| 2021-07-24 | 103.224.182.207 | ||||
| 2021-07-24 | 185.107.56.59 | ||||
| 2021-07-24 | 93.115.28.104 | ||||
| 2021-07-24 | 74.63.241.23 | ||||
| 2021-07-23 | 64.32.8.68 | ||||
| 2021-07-23 | 37.48.65.149 | ||||
| 2021-07-23 | 207.244.67.215 | ||||
| 2021-07-23 | 103.224.182.207 | ||||
| 2021-07-23 | 185.107.56.59 | ||||
| 2021-07-23 | 93.115.28.104 | ||||
| 2021-07-23 | 74.63.241.23 | ||||
| 2021-07-22 | 64.32.8.68 | ||||
| 2021-07-22 | 37.48.65.149 | ||||
| 2021-07-22 | 207.244.67.215 | ||||
| 2021-07-22 | 103.224.182.207 | ||||
| 2021-07-22 | 185.107.56.59 | ||||
| 2021-07-22 | 93.115.28.104 | ||||
| 2021-07-22 | 74.63.241.23 | ||||
| 2021-07-21 | 64.32.8.68 | ||||
| 2021-07-21 | 37.48.65.149 | ||||
| 2021-07-21 | 207.244.67.215 | ||||
| 2021-07-21 | 103.224.182.207 | ||||
| 2021-07-21 | 185.107.56.59 | ||||
| 2021-07-21 | 93.115.28.104 | ||||
| 2021-07-21 | 74.63.241.23 | ||||
| 2021-07-20 | 64.32.8.68 | ||||
| 2021-07-20 | 37.48.65.149 | ||||
| 2021-07-20 | 207.244.67.215 | ||||
| 2021-07-20 | 103.224.182.207 | ||||
| 2021-07-20 | 185.107.56.59 | ||||
| 2021-07-20 | 93.115.28.104 | ||||
| 2021-07-20 | 74.63.241.23 | ||||
| 2021-07-19 | 64.32.8.68 | ||||
| 2021-07-19 | 37.48.65.149 | ||||
| 2021-07-19 | 207.244.67.215 | ||||
| 2021-07-19 | 103.224.182.207 | ||||
| 2021-07-19 | 185.107.56.59 | ||||
| 2021-07-19 | 93.115.28.104 | ||||
| 2021-07-19 | 74.63.241.23 | ||||
| 2021-07-18 | 64.32.8.68 | ||||
| 2021-07-18 | 37.48.65.149 | ||||
| 2021-07-18 | 207.244.67.215 | ||||
| 2021-07-18 | 103.224.182.207 | ||||
| 2021-07-18 | 185.107.56.59 | ||||
| 2021-07-18 | 93.115.28.104 | ||||
| 2021-07-18 | 74.63.241.23 | ||||
| 2021-07-17 | 64.32.8.68 | ||||
| 2021-07-17 | 37.48.65.149 | ||||
| 2021-07-17 | 207.244.67.215 | ||||
| 2021-07-17 | 103.224.182.207 | ||||
| 2021-07-17 | 185.107.56.59 | ||||
| 2021-07-17 | 93.115.28.104 | ||||
| 2021-07-17 | 74.63.241.23 | ||||
| 2021-07-16 | 64.32.8.68 | ||||
| 2021-07-16 | 37.48.65.149 | ||||
| 2021-07-16 | 207.244.67.215 | ||||
| 2021-07-16 | 103.224.182.207 | ||||
| 2021-07-16 | 185.107.56.59 | ||||
| 2021-07-16 | 93.115.28.104 | ||||
| 2021-07-16 | 74.63.241.23 | ||||
| 2021-07-15 | 64.32.8.68 | ||||
| 2021-07-15 | 37.48.65.149 | ||||
| 2021-07-15 | 207.244.67.215 | ||||
| 2021-07-15 | 103.224.182.207 | ||||
| 2021-07-15 | 185.107.56.59 | ||||
| 2021-07-15 | 93.115.28.104 | ||||
| 2021-07-15 | 74.63.241.23 | ||||
| 2021-07-14 | 64.32.8.68 | ||||
| 2021-07-14 | 37.48.65.149 | ||||
| 2021-07-14 | 207.244.67.215 | ||||
| 2021-07-14 | 103.224.182.207 | ||||
| 2021-07-14 | 185.107.56.59 | ||||
| 2021-07-14 | 93.115.28.104 | ||||
| 2021-07-14 | 74.63.241.23 | ||||
| 2021-07-13 | 64.32.8.68 | ||||
| 2021-07-13 | 37.48.65.149 | ||||
| 2021-07-13 | 207.244.67.215 | ||||
| 2021-07-13 | 103.224.182.207 | ||||
| 2021-07-13 | 185.107.56.59 | ||||
| 2021-07-13 | 93.115.28.104 | ||||
| 2021-07-13 | 74.63.241.23 | ||||
| 2021-07-12 | 64.32.8.68 | ||||
| 2021-07-12 | 37.48.65.149 | ||||
| 2021-07-12 | 207.244.67.215 | ||||
| 2021-07-12 | 103.224.182.207 | ||||
| 2021-07-12 | 185.107.56.59 | ||||
| 2021-07-12 | 93.115.28.104 | ||||
| 2021-07-12 | 74.63.241.23 | ||||
| 2021-07-11 | 64.32.8.68 | ||||
| 2021-07-11 | 37.48.65.149 | ||||
| 2021-07-11 | 207.244.67.215 | ||||
| 2021-07-11 | 103.224.182.207 | ||||
| 2021-07-11 | 185.107.56.59 | ||||
| 2021-07-11 | 93.115.28.104 | ||||
| 2021-07-11 | 74.63.241.23 | ||||
| 2021-07-10 | 64.32.8.68 | ||||
| 2021-07-10 | 37.48.65.149 | ||||
| 2021-07-10 | 207.244.67.215 | ||||
| 2021-07-10 | 103.224.182.207 | ||||
| 2021-07-10 | 185.107.56.59 | ||||
| 2021-07-10 | 93.115.28.104 | ||||
| 2021-07-10 | 74.63.241.23 | ||||
| 2021-07-09 | 64.32.8.68 | ||||
| 2021-07-09 | 37.48.65.149 | ||||
| 2021-07-09 | 207.244.67.215 | ||||
| 2021-07-09 | 103.224.182.207 | ||||
| 2021-07-09 | 185.107.56.59 | ||||
| 2021-07-09 | 93.115.28.104 | ||||
| 2021-07-09 | 74.63.241.23 | ||||
| 2021-07-08 | 64.32.8.68 | ||||
| 2021-07-08 | 37.48.65.149 | ||||
| 2021-07-08 | 207.244.67.215 | ||||
| 2021-07-08 | 103.224.182.207 | ||||
| 2021-07-08 | 185.107.56.59 | ||||
| 2021-07-08 | 93.115.28.104 | ||||
| 2021-07-08 | 74.63.241.23 | ||||
| 2021-07-07 | 64.32.8.68 | ||||
| 2021-07-07 | 37.48.65.149 | ||||
| 2021-07-07 | 207.244.67.215 | ||||
| 2021-07-07 | 103.224.182.207 | ||||
| 2021-07-07 | 185.107.56.59 | ||||
| 2021-07-07 | 93.115.28.104 | ||||
| 2021-07-07 | 74.63.241.23 | ||||
| 2021-07-06 | 64.32.8.68 | ||||
| 2021-07-06 | 37.48.65.149 | ||||
| 2021-07-06 | 207.244.67.215 | ||||
| 2021-07-06 | 103.224.182.207 | ||||
| 2021-07-06 | 185.107.56.59 | ||||
| 2021-07-06 | 93.115.28.104 | ||||
| 2021-07-06 | 74.63.241.23 | ||||
| 2021-07-05 | 64.32.8.68 | ||||
| 2021-07-05 | 37.48.65.149 | ||||
| 2021-07-05 | 207.244.67.215 | ||||
| 2021-07-05 | 103.224.182.207 | ||||
| 2021-07-05 | 185.107.56.59 | ||||
| 2021-07-05 | 93.115.28.104 | ||||
| 2021-07-05 | 74.63.241.23 | ||||
| 2021-07-04 | 64.32.8.68 | ||||
| 2021-07-04 | 37.48.65.149 | ||||
| 2021-07-04 | 207.244.67.215 | ||||
| 2021-07-04 | 103.224.182.207 | ||||
| 2021-07-04 | 185.107.56.59 | ||||
| 2021-07-04 | 93.115.28.104 | ||||
| 2021-07-04 | 74.63.241.23 | ||||
| 2021-07-03 | 64.32.8.68 | ||||
| 2021-07-03 | 37.48.65.149 | ||||
| 2021-07-03 | 207.244.67.215 | ||||
| 2021-07-03 | 103.224.182.207 | ||||
| 2021-07-03 | 185.107.56.59 | ||||
| 2021-07-03 | 93.115.28.104 | ||||
| 2021-07-03 | 74.63.241.23 | ||||
| 2021-07-02 | 64.32.8.68 | ||||
| 2021-07-02 | 37.48.65.149 | ||||
| 2021-07-02 | 207.244.67.215 | ||||
| 2021-07-02 | 103.224.182.207 | ||||
| 2021-07-02 | 185.107.56.59 | ||||
| 2021-07-02 | 93.115.28.104 | ||||
| 2021-07-02 | 74.63.241.23 | ||||
| 2021-07-01 | 64.32.8.68 | ||||
| 2021-07-01 | 37.48.65.149 | ||||
| 2021-07-01 | 207.244.67.215 | ||||
| 2021-07-01 | 103.224.182.207 | ||||
| 2021-07-01 | 185.107.56.59 | ||||
| 2021-07-01 | 93.115.28.104 | ||||
| 2021-07-01 | 74.63.241.23 | ||||
| 2021-06-30 | 64.32.8.68 | ||||
| 2021-06-30 | 37.48.65.149 | ||||
| 2021-06-30 | 207.244.67.215 | ||||
| 2021-06-30 | 103.224.182.207 | ||||
| 2021-06-30 | 185.107.56.59 | ||||
| 2021-06-30 | 93.115.28.104 | ||||
| 2021-06-30 | 74.63.241.23 | ||||
| 2021-06-29 | 64.32.8.68 | ||||
| 2021-06-29 | 37.48.65.149 | ||||
| 2021-06-29 | 207.244.67.215 | ||||
| 2021-06-29 | 103.224.182.207 | ||||
| 2021-06-29 | 185.107.56.59 | ||||
| 2021-06-29 | 93.115.28.104 | ||||
| 2021-06-29 | 74.63.241.23 | ||||
| 2021-06-28 | 64.32.8.68 | ||||
| 2021-06-28 | 37.48.65.149 | ||||
| 2021-06-28 | 207.244.67.215 | ||||
| 2021-06-28 | 103.224.182.207 | ||||
| 2021-06-28 | 185.107.56.59 | ||||
| 2021-06-28 | 93.115.28.104 | ||||
| 2021-06-28 | 74.63.241.23 | ||||
| 2021-06-27 | 64.32.8.68 | ||||
| 2021-06-27 | 37.48.65.149 | ||||
| 2021-06-27 | 207.244.67.215 | ||||
| 2021-06-27 | 103.224.182.207 | ||||
| 2021-06-27 | 185.107.56.59 | ||||
| 2021-06-27 | 93.115.28.104 | ||||
| 2021-06-27 | 74.63.241.23 | ||||
| 2021-06-26 | 64.32.8.68 | ||||
| 2021-06-26 | 37.48.65.149 | ||||
| 2021-06-26 | 207.244.67.215 | ||||
| 2021-06-26 | 103.224.182.207 | ||||
| 2021-06-26 | 185.107.56.59 | ||||
| 2021-06-26 | 93.115.28.104 | ||||
| 2021-06-26 | 74.63.241.23 | ||||
| 2021-06-25 | 64.32.8.68 | ||||
| 2021-06-25 | 37.48.65.149 | ||||
| 2021-06-25 | 207.244.67.215 | ||||
| 2021-06-25 | 103.224.182.207 | ||||
| 2021-06-25 | 185.107.56.59 | ||||
| 2021-06-25 | 93.115.28.104 | ||||
| 2021-06-25 | 74.63.241.23 | ||||
| 2021-06-24 | 64.32.8.68 | ||||
| 2021-06-24 | 37.48.65.149 | ||||
| 2021-06-24 | 207.244.67.215 | ||||
| 2021-06-24 | 103.224.182.207 | ||||
| 2021-06-24 | 185.107.56.59 | ||||
| 2021-06-24 | 93.115.28.104 | ||||
| 2021-06-24 | 74.63.241.23 | ||||
| 2021-06-23 | 64.32.8.68 | ||||
| 2021-06-23 | 37.48.65.149 | ||||
| 2021-06-23 | 207.244.67.215 | ||||
| 2021-06-23 | 103.224.182.207 | ||||
| 2021-06-23 | 185.107.56.59 | ||||
| 2021-06-23 | 93.115.28.104 | ||||
| 2021-06-23 | 74.63.241.23 | ||||
| 2021-06-22 | 64.32.8.68 | ||||
| 2021-06-22 | 37.48.65.149 | ||||
| 2021-06-22 | 207.244.67.215 | ||||
| 2021-06-22 | 103.224.182.207 | ||||
| 2021-06-22 | 185.107.56.59 | ||||
| 2021-06-22 | 93.115.28.104 | ||||
| 2021-06-22 | 74.63.241.23 | ||||
| 2021-06-21 | 64.32.8.68 | ||||
| 2021-06-21 | 37.48.65.149 | ||||
| 2021-06-21 | 207.244.67.215 | ||||
| 2021-06-21 | 103.224.182.207 | ||||
| 2021-06-21 | 185.107.56.59 | ||||
| 2021-06-21 | 93.115.28.104 | ||||
| 2021-06-21 | 74.63.241.23 | ||||
| 2021-06-20 | 64.32.8.68 | ||||
| 2021-06-20 | 37.48.65.149 | ||||
| 2021-06-20 | 207.244.67.215 | ||||
| 2021-06-20 | 103.224.182.207 | ||||
| 2021-06-20 | 185.107.56.59 | ||||
| 2021-06-20 | 93.115.28.104 | ||||
| 2021-06-20 | 74.63.241.23 | ||||
| 2021-06-19 | 64.32.8.68 | ||||
| 2021-06-19 | 37.48.65.149 | ||||
| 2021-06-19 | 207.244.67.215 | ||||
| 2021-06-19 | 103.224.182.207 | ||||
| 2021-06-19 | 185.107.56.59 | ||||
| 2021-06-19 | 93.115.28.104 | ||||
| 2021-06-19 | 74.63.241.23 | ||||
| 2021-06-18 | 64.32.8.68 | ||||
| 2021-06-18 | 37.48.65.149 | ||||
| 2021-06-18 | 207.244.67.215 | ||||
| 2021-06-18 | 103.224.182.207 | ||||
| 2021-06-18 | 185.107.56.59 | ||||
| 2021-06-18 | 93.115.28.104 | ||||
| 2021-06-18 | 74.63.241.23 | ||||
| 2021-06-17 | 64.32.8.68 | ||||
| 2021-06-17 | 37.48.65.149 | ||||
| 2021-06-17 | 207.244.67.215 | ||||
| 2021-06-17 | 103.224.182.207 | ||||
| 2021-06-17 | 185.107.56.59 | ||||
| 2021-06-17 | 93.115.28.104 | ||||
| 2021-06-17 | 74.63.241.23 | ||||
| 2021-06-16 | 64.32.8.68 | ||||
| 2021-06-16 | 37.48.65.149 | ||||
| 2021-06-16 | 207.244.67.215 | ||||
| 2021-06-16 | 103.224.182.207 | ||||
| 2021-06-16 | 185.107.56.59 | ||||
| 2021-06-16 | 93.115.28.104 | ||||
| 2021-06-16 | 74.63.241.23 | ||||
| 2021-06-15 | 64.32.8.68 | ||||
| 2021-06-15 | 37.48.65.149 | ||||
| 2021-06-15 | 207.244.67.215 | ||||
| 2021-06-15 | 103.224.182.207 | ||||
| 2021-06-15 | 185.107.56.59 | ||||
| 2021-06-15 | 93.115.28.104 | ||||
| 2021-06-15 | 74.63.241.23 | ||||
| 2021-06-14 | 64.32.8.68 | ||||
| 2021-06-14 | 37.48.65.149 | ||||
| 2021-06-14 | 207.244.67.215 | ||||
| 2021-06-14 | 103.224.182.207 | ||||
| 2021-06-14 | 185.107.56.59 | ||||
| 2021-06-14 | 93.115.28.104 | ||||
| 2021-06-14 | 74.63.241.23 | ||||
| 2021-06-13 | 64.32.8.68 | ||||
| 2021-06-13 | 37.48.65.149 | ||||
| 2021-06-13 | 207.244.67.215 | ||||
| 2021-06-13 | 103.224.182.207 | ||||
| 2021-06-13 | 185.107.56.59 | ||||
| 2021-06-13 | 93.115.28.104 | ||||
| 2021-06-13 | 74.63.241.23 | ||||
| 2021-06-12 | 64.32.8.68 | ||||
| 2021-06-12 | 37.48.65.149 | ||||
| 2021-06-12 | 207.244.67.215 | ||||
| 2021-06-12 | 103.224.182.207 | ||||
| 2021-06-12 | 185.107.56.59 | ||||
| 2021-06-12 | 93.115.28.104 | ||||
| 2021-06-12 | 74.63.241.23 | ||||
| 2021-06-11 | 64.32.8.68 | ||||
| 2021-06-11 | 37.48.65.149 | ||||
| 2021-06-11 | 207.244.67.215 | ||||
| 2021-06-11 | 103.224.182.207 | ||||
| 2021-06-11 | 185.107.56.59 | ||||
| 2021-06-11 | 93.115.28.104 | ||||
| 2021-06-11 | 74.63.241.23 | ||||
| 2021-06-10 | 64.32.8.68 | ||||
| 2021-06-10 | 37.48.65.149 | ||||
| 2021-06-10 | 207.244.67.215 | ||||
| 2021-06-10 | 103.224.182.207 | ||||
| 2021-06-10 | 185.107.56.59 | ||||
| 2021-06-10 | 93.115.28.104 | ||||
| 2021-06-10 | 74.63.241.23 | ||||
| 2021-06-09 | 64.32.8.68 | ||||
| 2021-06-09 | 37.48.65.149 | ||||
| 2021-06-09 | 207.244.67.215 | ||||
| 2021-06-09 | 103.224.182.207 | ||||
| 2021-06-09 | 185.107.56.59 | ||||
| 2021-06-09 | 93.115.28.104 | ||||
| 2021-06-09 | 74.63.241.23 | ||||
| 2021-06-08 | 64.32.8.68 | ||||
| 2021-06-08 | 37.48.65.149 | ||||
| 2021-06-08 | 207.244.67.215 | ||||
| 2021-06-08 | 103.224.182.207 | ||||
| 2021-06-08 | 185.107.56.59 | ||||
| 2021-06-08 | 93.115.28.104 | ||||
| 2021-06-08 | 74.63.241.23 | ||||
| 2021-06-07 | 64.32.8.68 | ||||
| 2021-06-07 | 37.48.65.149 | ||||
| 2021-06-07 | 207.244.67.215 | ||||
| 2021-06-07 | 103.224.182.207 | ||||
| 2021-06-07 | 185.107.56.59 | ||||
| 2021-06-07 | 93.115.28.104 | ||||
| 2021-06-07 | 74.63.241.23 | ||||
| 2021-06-06 | 64.32.8.68 | ||||
| 2021-06-06 | 37.48.65.149 | ||||
| 2021-06-06 | 207.244.67.215 | ||||
| 2021-06-06 | 103.224.182.207 | ||||
| 2021-06-06 | 185.107.56.59 | ||||
| 2021-06-06 | 93.115.28.104 | ||||
| 2021-06-06 | 74.63.241.23 | ||||
| 2021-06-01 | 64.32.8.68 | ||||
| 2021-06-01 | 37.48.65.149 | ||||
| 2021-06-01 | 207.244.67.215 |